IDIQ Joins Identity Theft Resource Center in Releasing New Report on Trends in Identity Theft and Scams
Identity IQ
MAY 17, 2023
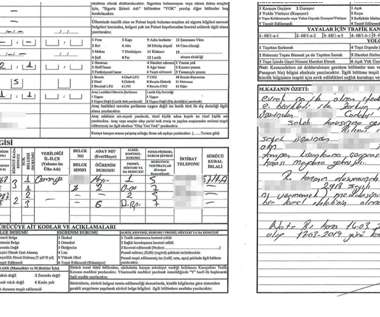
This report explores key findings based on contacts from nearly 15,000 reports to the ITRC of identity compromises, misuse, and abuse from individuals across the country. This report explores key findings based on contacts from nearly 15,000 reports to the ITRC of identity compromises, misuse, and abuse from individuals across the country.



















Let's personalize your content