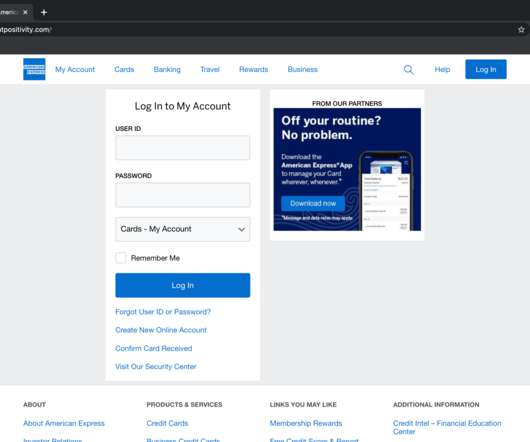
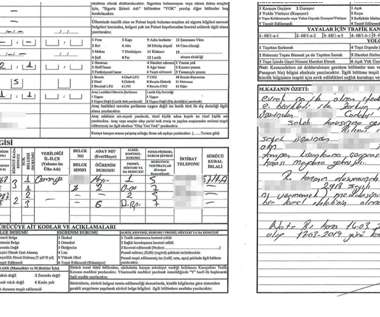
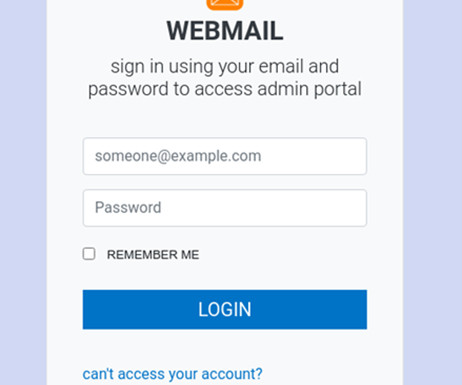
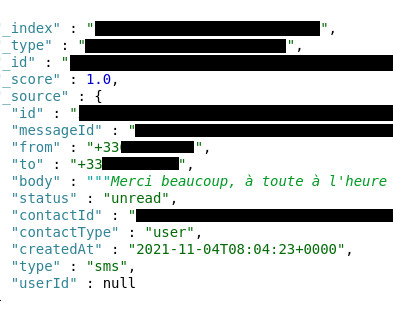
A new phishing scam targets American Express cardholders
Security Affairs
SEPTEMBER 5, 2022
Below are the recommendations provided by Armorblox to identify phishing messages: Augment native email security with additional controls; Watch out for social engineering cues; Follow multi-factor authentication and password management best practices; Follow me on Twitter: @securityaffairs and Facebook. Pierluigi Paganini.





















Let's personalize your content