6 Business functions that will benefit from cybersecurity automation
CyberSecurity Insiders
OCTOBER 28, 2021
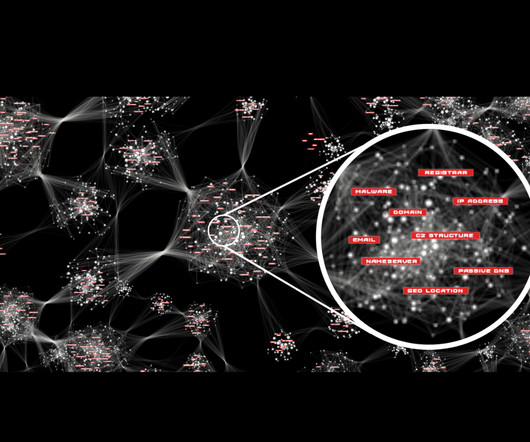
Cybersecurity automation gives organizations the ability to perform threat detection and incident response at scale. Many security professionals spend hours each day manually administering tools to protect enterprise data. For many organizations, spending so much time collecting data is not conducive to innovation and growth.























Let's personalize your content