Introducing continuous remote worker visibility and expanded data collection with Secure Network Analytics Release 7.3.2
Cisco Security
JUNE 1, 2021
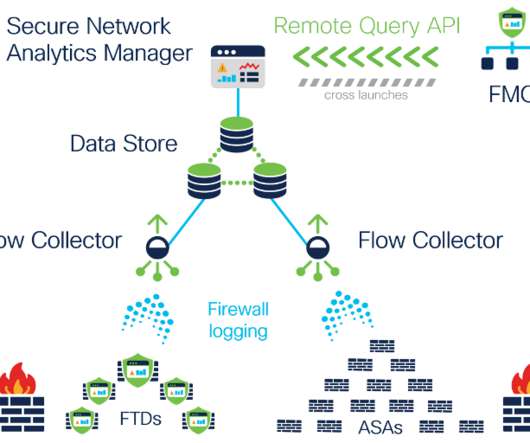
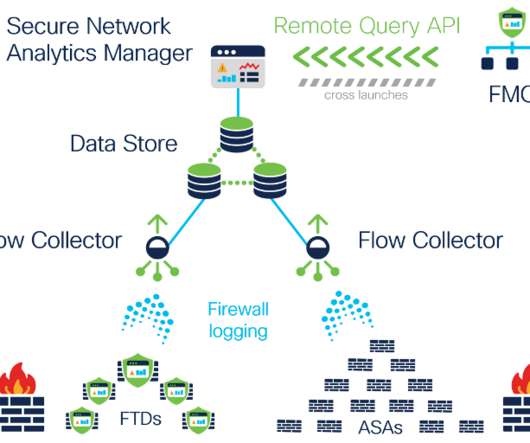
Organizations had always historically experienced visibility gaps into employee activities whenever their users were off-VPN while working remotely. we’re further extending this capability with the Data Store now supporting all NVM telemetry record collection to offer 100%-complete and continuous remote worker visibility.














Let's personalize your content