Trusted relationship attacks: trust, but verify
SecureList
MAY 28, 2024
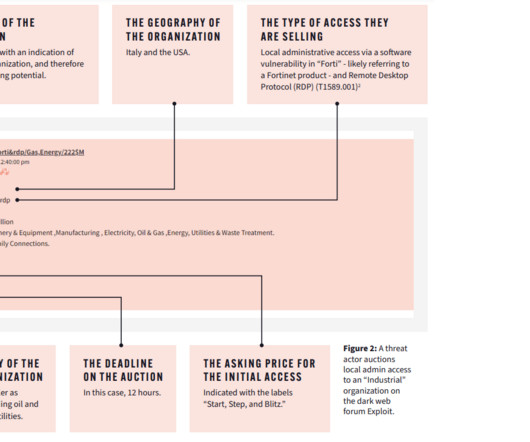
But along with the advantages, such as saved time and resources, delegating non-core tasks creates new challenges in terms of information security. Most often, communication between the service provider and the client takes place via VPN connections and Remote Desktop Protocol (RDP) services.













Let's personalize your content