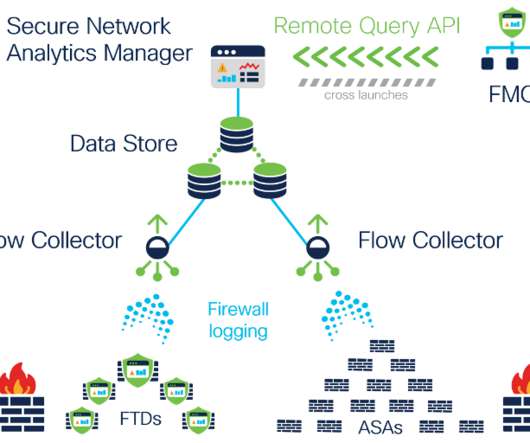
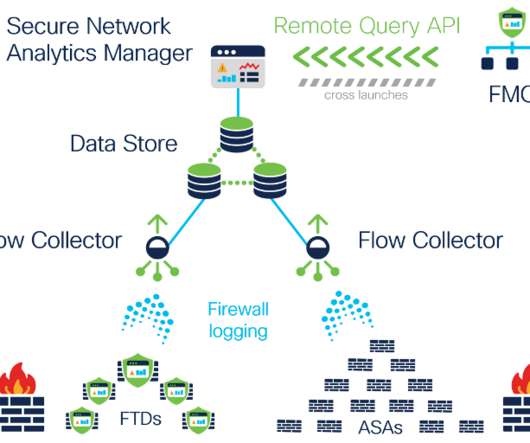
Introducing continuous remote worker visibility and expanded data collection with Secure Network Analytics Release 7.3.2
Cisco Security
JUNE 1, 2021
The ability to define customized security events based on NVM data-specific criteria. A Secure Network Analytics deployment enabled with both the AnyConnect Secure Mobility Client and the Data Store. Expanded data collection to provide further extended visibility and enhanced context . With release 7.3.2,



















Let's personalize your content