Overview of IoT threats in 2023
SecureList
SEPTEMBER 21, 2023
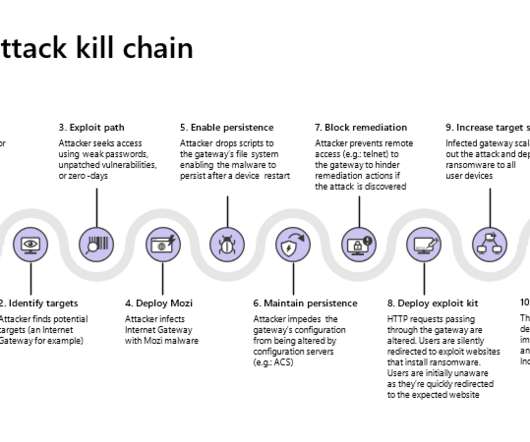
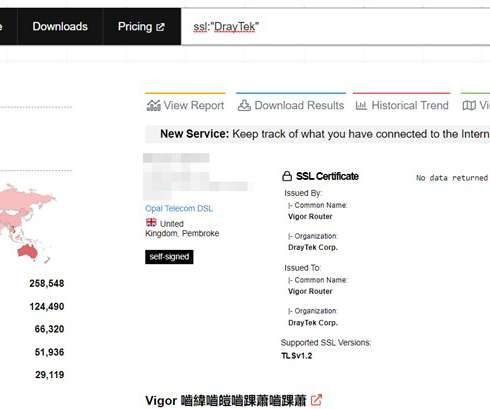
Attack vectors There are two main IoT infection routes: brute-forcing weak passwords and exploiting vulnerabilities in network services. A successful password cracking enables hackers to execute arbitrary commands on a device and inject malware. Unfortunately, users tend to leave these passwords unchanged. Our advantages: 1.















Let's personalize your content