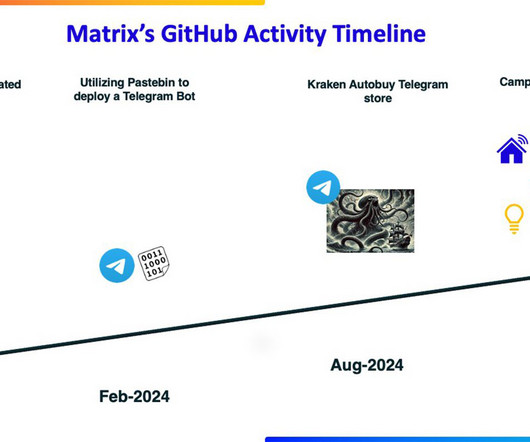
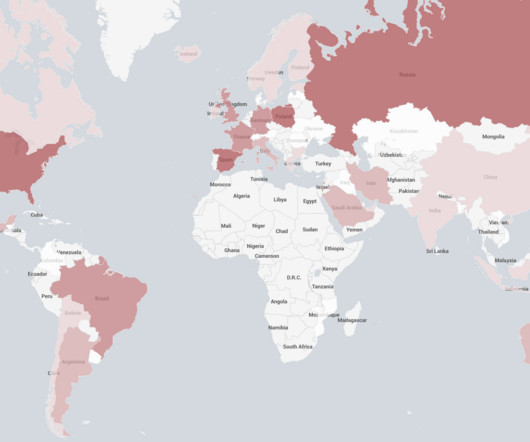
35 Million Devices Vulnerable: Matrix DDoS Campaign Highlights Growing IoT Threat
Penetration Testing
NOVEMBER 27, 2024
Aqua Nautilus researchers have uncovered a major Distributed Denial-of-Service (DDoS) campaign led by a threat actor operating under the name Matrix.


























Let's personalize your content