Security Affairs newsletter Round 498 by Pierluigi Paganini – INTERNATIONAL EDITION
Security Affairs
NOVEMBER 17, 2024
CISA adds Palo Alto Networks Expedition bugs to its Known Exploited Vulnerabilities catalog Hackers target critical flaw CVE-2024-10914 in EOL D-Link NAS Devices China-linked threat actors compromised multiple telecos and spied on a limited number of U.S.








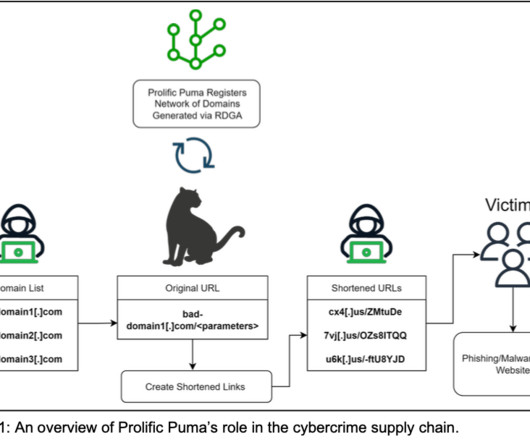









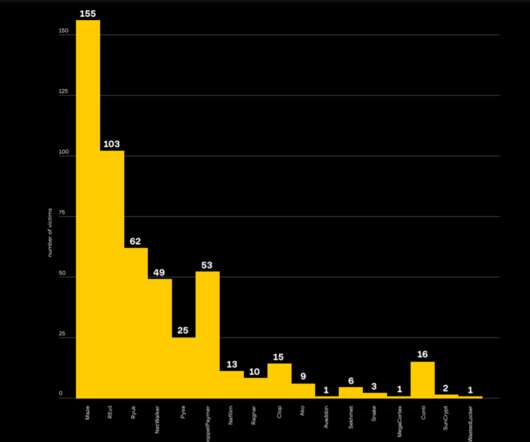








Let's personalize your content