European firm DSIRF behind the attacks with Subzero surveillance malware
Security Affairs
JULY 28, 2022
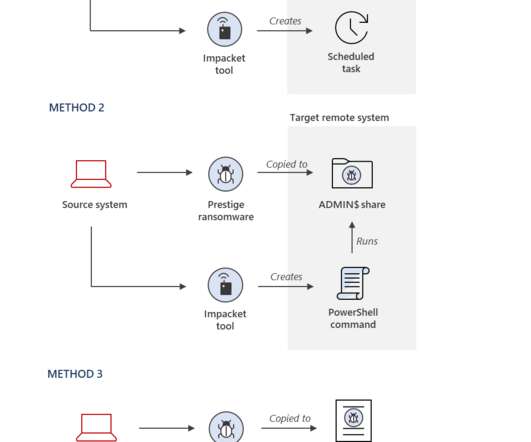
Microsoft linked a private-sector offensive actor (PSOA) to attacks using multiple zero-day exploits for its Subzero malware. Microsoft states that multiple news reports have linked the company to the Subzero malware toolset used to hack a broad range of devices, phones, computers, and network and internet-connected devices.












Let's personalize your content