US Feds arrested two men involved in the Warzone RAT operation
Security Affairs
FEBRUARY 12, 2024
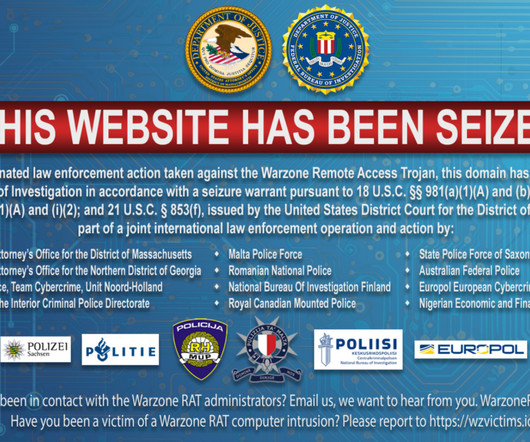
. “According to court documents authorizing the seizures, the Warzone RAT provided cybercriminals the ability to browse victim file systems, take screenshots, record keystrokes, steal victim usernames and passwords, and watch victims through their web cameras, all without the victims’ knowledge or permission.”
















Let's personalize your content