Inserting a Backdoor into a Machine-Learning System
Schneier on Security
OCTOBER 11, 2022
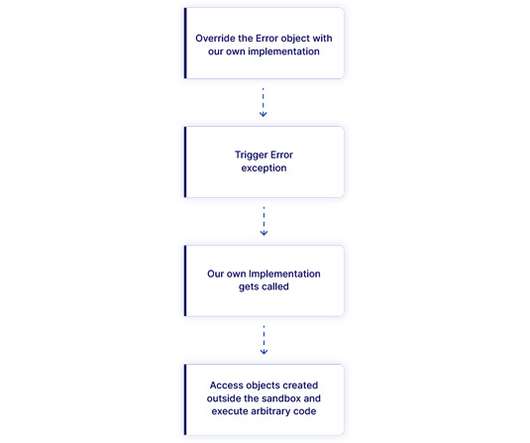
Interesting research: “ ImpNet: Imperceptible and blackbox-undetectable backdoors in compiled neural networks , by Tim Clifford, Ilia Shumailov, Yiren Zhao, Ross Anderson, and Robert Mullins: Abstract : Early backdoor attacks against machine learning set off an arms race in attack and defence development. Defences have since appeared demonstrating some ability to detect backdoors in models or even remove them.







































Let's personalize your content