Looking Back at the Colonial Pipeline Ransomware Incident
Lohrman on Security
MAY 8, 2022
In early May 2021, the world was shocked into attention by a ransomware attack that brought down gas lines. What have we learned — or not — one year later?
Lohrman on Security
MAY 8, 2022
In early May 2021, the world was shocked into attention by a ransomware attack that brought down gas lines. What have we learned — or not — one year later?

Security Affairs
MAY 8, 2022
This post provides a timeline of the events related to Russia invasion of Ukraine from the cyber security perspective. Below is the timeline of the events related to the ongoing Russia invasion that occurred in the previous weeks: May 06 – Anonymous and Ukraine IT Army continue to target Russian entities. The Anonymous collective and the volunteer group Ukraine IT Army continues to launch cyber attacks on Russian entities.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
MAY 8, 2022
While we recently “ celebrated ” World Password Day, almost every security outlet keeps telling us that passwords alone are not enough. In practice, in the last few years this has meant pairing passwords with something else, such as a one-time code from an app or an SMS message, in a scheme called two-factor authentication ( 2FA ). But while pairing passwords with a second factor is much better than using a password by itself, it is just a way of working around some very serious, inh
Security Affairs
MAY 8, 2022
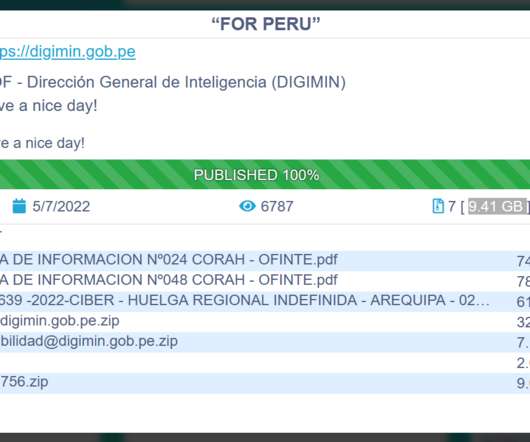
Conti Ransomware gang claims to have hacked the Peru MOF – Dirección General de Inteligencia (DIGIMIN) and stolen 9.41 GB. The Conti ransomware gang added the Peru MOF – Dirección General de Inteligencia (DIGIMIN) to the list of its victims on its Tor leak site. The National Directorate of Intelligence is the premier intelligence agency in Peru.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Security Boulevard
MAY 8, 2022
In the world of cybersecurity, various types of penetration testing exist, but before we explore the various kinds, what is penetration testing? A penetration test intends to identify network, system, or application vulnerabilities of an organization. These loopholes are then shared with decision-makers, who choose whether or not to rectify them. A penetration tester submits […].

Security Affairs
MAY 8, 2022
The American agricultural machinery manufacturer AGCO announced that has suffered a ransomware attack that impacted its production facilities. AGCO, one of the most important agricultural machinery manufacturers, announced that a ransomware attack impacted some of its production facilities. The company was forced to shut down portions of its IT systems in response to the incident.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Affairs
MAY 8, 2022
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. Raspberry Robin spreads via removable USB devices Malware campaign hides a shellcode into Windows event logs US gov sanctions cryptocurrency mixer Blender also used by North Korea-linked Lazarus APT How the thriving fraud industry within Facebook a
The Hacker News
MAY 8, 2022
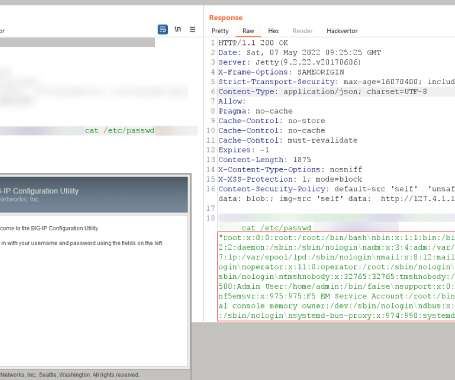
Days after F5 released patches for a critical remote code execution vulnerability affecting its BIG-IP family of products, security researchers are warning that they were able to create an exploit for the shortcoming. Tracked CVE-2022-1388 (CVSS score: 9.

Security Boulevard
MAY 8, 2022
In early May 2021, the world was shocked into attention by a ransomware attack that brought down gas lines. What have we learned — or not — one year later? The post Looking Back at the Colonial Pipeline Ransomware Incident appeared first on Security Boulevard.

The Hacker News
MAY 8, 2022
The U.S. State Department has announced rewards of up to $10 million for any information leading to the identification of key individuals who are part of the infamous Conti cybercrime gang. Additionally, it's offering another $5 million for intelligence information that could help arrest or convict individuals who are conspiring or attempting to affiliate with the group in a ransomware attack.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Affairs
MAY 8, 2022
The US Government offers up to $15 million for information that helps identify and locate leadership and co-conspirators of the Conti ransomware gang. The US Department of State offers up to $15 million for information that helps identify and locate leadership and co-conspirators of the Conti ransomware gang. The reward is offered under the Department of State’s Transnational Organized Crime Rewards Program (TOCRP).

Bleeping Computer
MAY 8, 2022
Security researchers are warning F5 BIG-IP admins to immediately install the latest security updates after creating exploits for a recently disclosed critical CVE-2022-1388 remote code execution vulnerability. [.].

Tech Republic Security
MAY 8, 2022
Bridgecrew by Prisma Cloud is the codified cloud security platform built to bridge the gap between DevOps and security teams. Powered by automation, Bridgecrew empowers teams to find, fix, and prevent vulnerabilities, misconfigurations, and license compliance issues in source code, containerized applications, and infrastructure as code. With Bridgecrew’s platform, teams can streamline cloud security, enforce.

Bleeping Computer
MAY 8, 2022
The RubyGems package repository has fixed a critical vulnerability that would allow anyone to unpublish ("yank") certain Ruby packages from the repository and republish their tainted or malicious versions with the same file names and version numbers. [.].

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Boulevard
MAY 8, 2022
Josh Feinblum is the co-founder of Stavvy, a Boston-based fully integrated digital mortgage platform, where he leads product, engineering, people, and finance. He also serves as a venture partner at F-Prime Capital, where he evaluates and advises startups of all stages across multiple verticals. Josh talks to us about his journey through cybersecurity including his […].

Bleeping Computer
MAY 8, 2022
A credit card stealing service is growing in popularity, allowing any low-skilled threat actors an easy and automated way to get started in the world of financial fraud. [.].

Security Boulevard
MAY 8, 2022
Most people preferred to download a virtual image of Kali Linux. The virtual machine is the best option to use multiple operating systems at a time. Kali Linux is the best operating system mostly used by hackers and penetration testers. On the official Kali Linux website, Virtual images are available for VMware and Virtual Box. […]. The post How to Download Virtual Image of Kali Linux appeared first on Security Boulevard.

The Security Ledger
MAY 8, 2022
A cyber attack has disrupted the operations of AGCO/Fendt, a major manufacturer of agricultural equipment, the company has acknowledged. The post Cyber Attack Halts Production at Ag Equipment Maker AGCO Fendt appeared first on The Security Ledger with Paul F. Roberts. Related Stories Feel Good Ukraine Tractor Story Highlights Ag Cyber Risk DEF CON: Security Holes in Deere, Case IH Shine Spotlight on Agriculture Cyber Risk Episode 218: Denial of Sustenance Attacks -The Cyber Risk To Agriculture.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Security Boulevard
MAY 8, 2022
Visit SecZetta in Person at Booth #7 and attend two speaking sessions 10-13, May, 2022, | Berlin Congress Center| Berlin, Germany & Online Fall River, Mass. May 6, 2022. The post SecZetta Brings Third-Party Identity Risk Solution to KuppingerCole European Identity Conference 2022 appeared first on SecZetta. The post SecZetta Brings Third-Party Identity Risk Solution to KuppingerCole European Identity Conference 2022 appeared first on Security Boulevard.

Security Affairs
MAY 8, 2022
The National Institute of Standards and Technology (NIST) has released updated guidance for defending against supply-chain attacks. The National Institute of Standards and Technology (NIST) has released updated guidance for defending against supply chain attacks. NIST has published the “ Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations ” in response to the Executive Order 14028: Improving the Nation’s Cybersecurity. “The purpose of this p

Security Boulevard
MAY 8, 2022
Visit SecZetta in Person at Booth #803 12-13 May| InterContinental London – The O2| London, England Fall River, Mass. (May 06, 2022) – Join SecZetta at the Gartner Identity. The post SecZetta Brings Third-Party Identity Solution to Gartner Identity & Access Management Summit 2022 appeared first on SecZetta. The post SecZetta Brings Third-Party Identity Solution to Gartner Identity & Access Management Summit 2022 appeared first on Security Boulevard.
Security Boulevard
MAY 8, 2022
via the comic artistry and dry wit of Randall Munroe , resident at XKCD ! Permalink. The post XKCD ‘Deep End’ appeared first on Security Boulevard.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
MAY 8, 2022
Global AppSec US 2021 Virtual Conference] 2 for publishing their well-crafted application security videos on the organization’s’ YouTube ** channel. Permalink. The post OWASP® Global AppSec US 2021 Virtual – Karthik Krishnamo’s ‘Application Security Playbook For Business’ appeared first on Security Boulevard.

Security Boulevard
MAY 8, 2022
Our thanks to both the OWASP® Foundation and the OWASP Global AppSec US 2021 Virtual Conference for publishing their well-crafted application security videos on the organization’s’ YouTube channel. Permalink. The post OWASP® Global AppSec US 2021 Virtual – Kim Carter’s ‘Purple Teaming With OWASP® PurpleTeam’ appeared first on Security Boulevard.
Let's personalize your content