Weekly Update 293
Troy Hunt
APRIL 30, 2022
Didn't get a lot done this week, unless you count scuba diving, snorkelling, spear fishing and laying around on tropical sand cays 😎 This week is predominantly about the time we just spent up on the Great Barrier Reef which has very little relevance to infosec, IoT, 3D printing and the other usual topics. But as I refer to in the guitar lessons blog post referenced below, I share what I do pretty transparently and organically and this week, that's what I want to talk about.





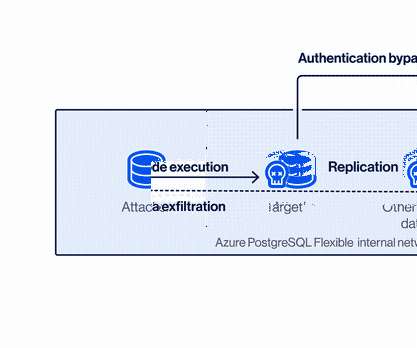

















Let's personalize your content