T-Mobile confirms Lapsus$ had access its systems
Security Affairs
APRIL 23, 2022
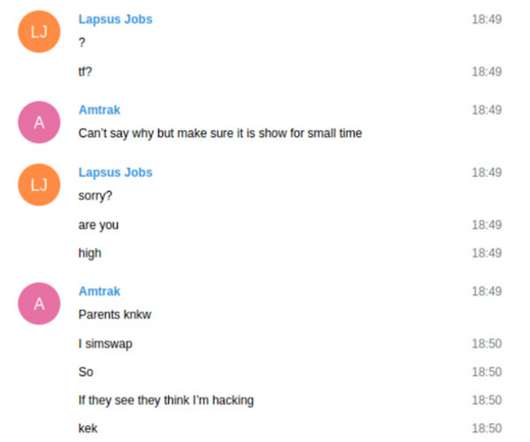
Telecommunication giant T-Mobile confirmed the LAPSUS$ extortion group gained access to its networks in March. Telecom company T-Mobile on Friday revealed that LAPSUS$ extortion gang gained access to its networks. The popular investigator and journalist Brian Krebs first surmised that the LAPSUS$ gang has breached T-Mobile after he reviewed a copy of the private chat messages between members of the cybercrime group.

















Let's personalize your content