Have I Been Pwned 2.0 is Now Live!
Troy Hunt
MAY 19, 2025
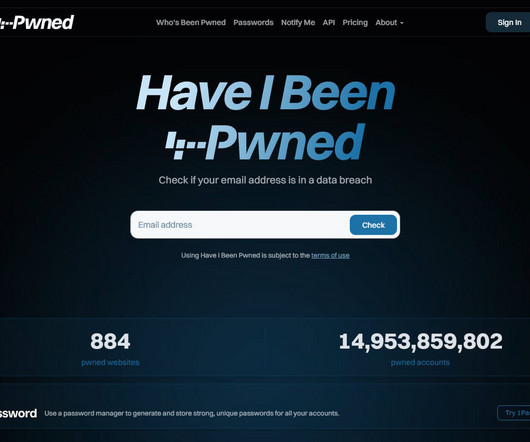
This has been a very long time coming, but finally, after a marathon effort, the brand new Have I Been Pwned website is now live ! Feb last year is when I made the first commit to the public repo for the rebranded service, and we soft-launched the new brand in March of this year. Over the course of this time, we've completely rebuilt the website, changed the functionality of pretty much every web page, added a heap of new features, and today, we're even launching a merch store 😎







































Let's personalize your content