Backdoor by Design: Malicious npm Packages Hijack Cursor IDE on macOS
Penetration Testing
MAY 10, 2025
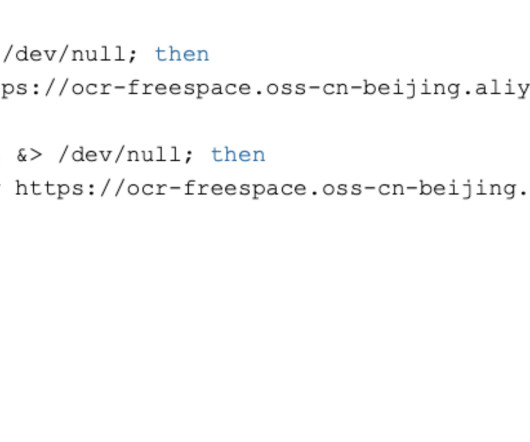
The Socket Threat Research Team has uncovered a sophisticated campaign targeting macOS users of the Cursor AI code The post Backdoor by Design: Malicious npm Packages Hijack Cursor IDE on macOS appeared first on Daily CyberSecurity.


































Let's personalize your content