What’s New in the NIST Cybersecurity Framework 2.0 Draft?
Lohrman on Security
AUGUST 27, 2023
NIST has released a draft version 2.0 of the Cybersecurity Framework. Here’s what you need to know and how to get your recommendations included.

Lohrman on Security
AUGUST 27, 2023
NIST has released a draft version 2.0 of the Cybersecurity Framework. Here’s what you need to know and how to get your recommendations included.

Bleeping Computer
AUGUST 27, 2023
Microsoft is experimenting with different approaches to introduce new users to Windows 11's features as soon as they complete the initial setup, also known as the "Out of Box Experience" (OOBE). [.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Hacker News
AUGUST 27, 2023
An updated version of a botnet malware called KmsdBot is now targeting Internet of Things (IoT) devices, simultaneously branching out its capabilities and the attack surface. "The binary now includes support for Telnet scanning and support for more CPU architectures," Akamai security researcher Larry W. Cashdollar said in an analysis published this month.

Security Boulevard
AUGUST 27, 2023
NIST has released a draft version 2.0 of the Cybersecurity Framework. Here’s what you need to know and how to get your recommendations included. The post What’s New in the NIST Cybersecurity Framework 2.0 Draft? appeared first on Security Boulevard.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

WIRED Threat Level
AUGUST 27, 2023
The sabotage of more than 20 trains in Poland by apparent supporters of Russia was carried out with a simple “radio-stop” command anyone could broadcast with $30 in equipment.
Security Affairs
AUGUST 27, 2023
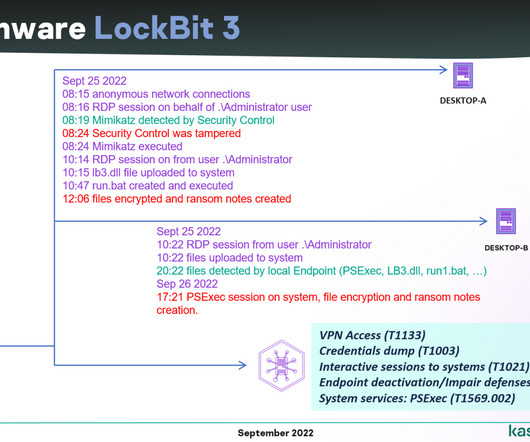
The leak of the source code of the LockBit 3.0 ransomware builder in 2022 allowed threat actors to create new variants of the threat. Lockbit v3 , aka Lockbit Black , was detected in June 2022, but in September 2022 a builder for this variant was leaked online. The availability of the builder allowed anyone to create their own customized version of the ransomware.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Affairs
AUGUST 27, 2023
Cisco addressed three high-severity flaws in NX-OS and FXOS software that could cause denial-of-service (DoS) conditions. Cisco this week addressed multiple flaws in its products, including three high-severity flaws in NX-OS and FXOS software. An attacker can exploit these three issues to cause a denial-of-service (DoS) condition. Below is the list of flaws addressed by the vendor as part of the company’s semiannual FXOS and NX-OS Software Security Advisory Bundled Publication on August 23

Bleeping Computer
AUGUST 27, 2023
The Rhysida ransomware gang has claimed responsibility for the massive cyberattack on Prospect Medical Holdings, claiming to have stolen 500,000 social security numbers, corporate documents, and patient records. [.

Security Affairs
AUGUST 27, 2023
The Polish domestic security agency is investigating a hacking attack on the national railways, Polish media report. Poland’s Internal Security Agency (ABW) and national police have launched an investigation into a hacking attack on the state’s railway network. According to the Polish Press Agency, the attack disrupted the traffic overnight last week.

WIRED Threat Level
AUGUST 27, 2023
A ramshackle team of American scientists scrambled to decode the Nazi cipher before the time ran out. Luckily, they had a secret weapon.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
Malwarebytes
AUGUST 27, 2023
Last week on Malwarebytes Labs: Teenage members of Lapsus$ ransomware gang convicted Update now! Google Chrome's first weekly update has arrived Smart lightbulb and app vulnerability puts your Wi-Fi password at risk Malwarebytes acquires Cyrus Security Ivanti Sentry critical vulnerability—don't play dice, patch DarkGate reloaded via malvertising and SEO poisoning campaigns Adobe ColdFusion vulnerability exploited in the wild Alert Prioritization and Guided Remediation: The future of EDR Up

Graham Cluley
AUGUST 27, 2023
Graham Cluley Security News is sponsored this week by the folks at PlexTrac. Thanks to the great team there for their support! If you are investing in solutions for continuous assessment and validation or breach and attack simulation, you know that managing the data and remediation efforts necessary to make real progress can be overwhelming. … Continue reading "Ready to enhance your continuous assessment efforts?

Security Boulevard
AUGUST 27, 2023
Many thanks to BSides Cheltenham for publishing their presenter’s outstanding BSides Cheltenham 2023 security content on the organizations’ YouTube channel. Permalink The post BSides Cheltenham 2023 – Simon Gurney – Making Your Own Cool Conference Badges! appeared first on Security Boulevard.

Troy Hunt
AUGUST 27, 2023
Somehow in this week's video, I forgot to talk about the single blog post I wrote this week! So here's the elevator pitch: Cloudflare's Turnstile is a bot-killing machine I've had enormous success with for the "API" (quoted because it's not meant to be consumed by others), behind the front page of HIBP. It's unintrusive, is super easy to implement and kills bots dead.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Affairs
AUGUST 27, 2023
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Cloud and hosting provider Leaseweb took down critical systems after a cyber attack French employment agency Pôle emploi data breach impacted 10M people Crypto investor data exposed by a SIM swapping attack against a Kroll employee China-linked Fl
Let's personalize your content