From Progress to Bans: How Close Are Human Microchip Implants?
Lohrman on Security
FEBRUARY 5, 2023
A lot has happened in the past 12 months regarding human microchip implants. Here’s your roundup of recent developments.

Lohrman on Security
FEBRUARY 5, 2023
A lot has happened in the past 12 months regarding human microchip implants. Here’s your roundup of recent developments.
Krebs on Security
FEBRUARY 5, 2023
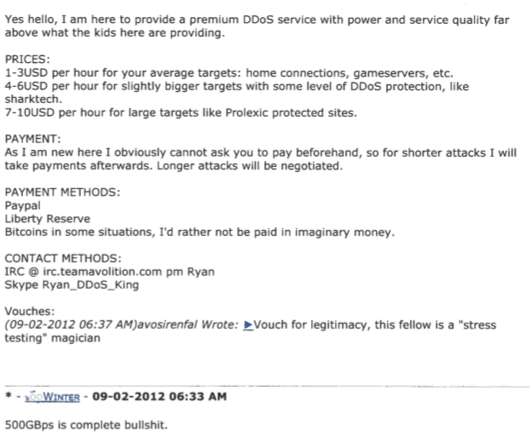
Julius “Zeekill” Kivimäki, a 25-year-old Finnish man charged with extorting a local online psychotherapy practice and leaking therapy notes for more than 22,000 patients online, was arrested this week in France. A notorious hacker convicted of perpetrating tens of thousands of cybercrimes, Kivimäki had been in hiding since October 2022, when he failed to show up in court and Finland issued an international warrant for his arrest.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
FEBRUARY 5, 2023
Researchers at IT security company Check Point security have flagged Dingo Token as a potential scam after finding a function that allows the project's owner to manipulate trading fees up to 99% of the transaction value. [.

Security Affairs
FEBRUARY 5, 2023
Microsoft attributes a recent cyber attack against the satirical French magazine Charlie Hebdo to an Iran-linked NEPTUNIUM APT group. Microsoft’s Digital Threat Analysis Center (DTAC) attributes a recent cyberattacks against the satirical French magazine Charlie Hebdo to an Iran-linked threat actor tracked as NEPTUNIUM (aka Emennet Pasargad , Holy Souls).

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Security Boulevard
FEBRUARY 5, 2023
The attacks on password managers and their users continue as Bitwarden and 1Password users have reported seeing paid ads for phishing sites in Google search results for the official login page of the password management vendors. Not only that, a new vulnerability in the popular open-source password management software KeePass has also been reported.

Bleeping Computer
FEBRUARY 5, 2023
Royal Ransomware is the latest ransomware operation to add support for encrypting Linux devices to its most recent malware variants, specifically targeting VMware ESXi virtual machines. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
SecureWorld News
FEBRUARY 5, 2023
As early as 1950, visionary computer scientists like Alan Turing speculated about the possibility of machines that could interpret instructions and learn new skills like the human mind. Now, a few cheesy sci-fi movies later, functional examples of artificial intelligence are becoming an increasingly common part of our day to day lives. One of the biggest developments in mainstream artificial intelligence (AI) to happen in recent years has been the launch of ChatGPT , a language-learning model th

Security Boulevard
FEBRUARY 5, 2023
The promise of quantum computing is tantalizing. Once quantum machines become sufficiently powerful, tasks that would have taken hundreds or thousands of years using traditional binary computers might instead be completed in days or even hours. The post Let’s Talk About the Upside of Quantum Computing appeared first on Keyfactor. The post Let’s Talk About the Upside of Quantum Computing appeared first on Security Boulevard.

Malwarebytes
FEBRUARY 5, 2023
Last week on Malwarebytes Labs: A private moment, caught by a Roomba, ended up on Facebook. Eileen Guo explains how: Lock and Code S04E03 New data wipers deployed against Ukraine Update your LearnPress plugins now! Riot Games refuses to pay ransom to avoid League of Legends leak Analyzing and remediating a malware infested T95 TV box from Amazon Google sponsored ads malvertising targets password manager 40% of online shops tricking users with "dark patterns" How to protect your business from sup

Bleeping Computer
FEBRUARY 5, 2023
Dashlane announced it had made the source code for its Android and iOS apps available on GitHub under the Creative Commons Attribution-NonCommercial 4.0 license. [.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Boulevard
FEBRUARY 5, 2023
A lot has happened in the past 12 months regarding human microchip implants. Here’s your roundup of recent developments. The post From Progress to Bans: How Close Are Human Microchip Implants? appeared first on Security Boulevard.

Malwarebytes
FEBRUARY 5, 2023
On Friday and over the weekend, several Computer Emergency Response Teams (CERTs) sounded the alarm about an ongoing large scale ransomware attack on VMware ESXi virtual machines. With some discrepancies between Shodan queries from various researchers, most agree that an estimated 500 entities were affected by the attack over the weekend. Old vulnerability The suspected vulnerability, which is listed as CVE-2021-21974 was patched by VMware almost two years ago.
Spinone
FEBRUARY 5, 2023
About 25% of all data breaches are caused by human error. Phishing attacks are one of the main cyber threats involving mistakes by workers. Arranging training for your employees is a great way to protect your company against phishing and its expensive and time-consuming consequences. So, let’s take a look at notable phishing awareness training […] The post Phishing Awareness Training: Best Providers 2023 first appeared on SpinOne.

Security Boulevard
FEBRUARY 5, 2023
The masked Aadhaar is a variant form of Aadhaar that the Unique Identification Authority of India (UIDAI) developed after taking into account the issue of data privacy for individuals. Read through to know more about what it is. What is a Masked Aadhaar? You can hide your Aadhaar number in your downloaded e-Aadhaar by selecting […] The post Why is Aadhaar Masking important?

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Spinone
FEBRUARY 5, 2023
This article provides a detailed backup comparison checklist to help SMBs choose a backup tool that will meet their needs. Why are cloud SaaS backups essential? The business continuity of present-day SMBs is extremely dependent on cloud data security now that a significant portion of it is housed in SaaS environments. Today, some businesses run […] The post Comprehensive Backup Comparison Checklist for SMBs 2023 first appeared on SpinOne.

Security Boulevard
FEBRUARY 5, 2023
Our thanks to USENIX for publishing their Presenter’s outstanding USENIX Security ’22 Conference content on the organization’s’ YouTube channel. Permalink The post USENIX Security ’22 – Huiying Li, Shawn Shan, Emily Wenger, Jiayun Zhang, Haitao Zheng, Ben Y. Zhao – ‘Blacklight: Scalable Defense for Neural Networks against Query-Based Black-Box Attacks’ appeared first on Security Boulevard.

Security Affairs
FEBRUARY 5, 2023
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. CISA adds Oracle, SugarCRM bugs to its Known Exploited Vulnerabilities Catalog GoAnywhere MFT zero-day flaw actively exploited CERT-FR warns of a new wave of ransomware attacks targeting VMware ESXi servers Tallahassee Memorial HealthCare, Florida,
Security Boulevard
FEBRUARY 5, 2023
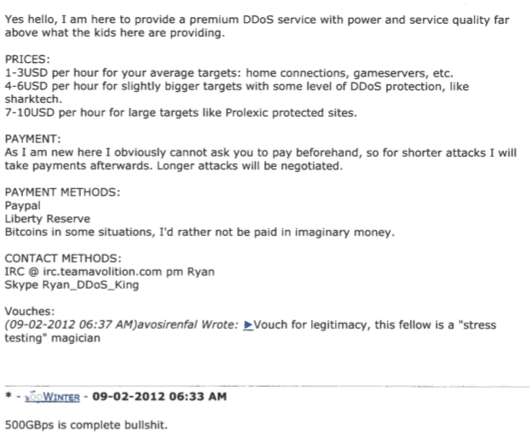
Julius "Zeekill" Kivimäki, a 25-year-old Finnish man charged with extorting a local online psychotherapy practice and leaking therapy notes for more than 22,000 patients online, was arrested this week in France. A notorious hacker convicted of perpetrating tens of thousands of cybercrimes, Kivimäki had been in hiding since October 2022, when he failed to show up in court and Finland issued an international warrant for his arrest.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

The Security Ledger
FEBRUARY 5, 2023
A school that never sleeps? Cameras that go dark? A dead company hacked back to life? Welcome to the growing Internet of Zombie devices that threatens the security of the Internet. The post Forget the IoT. Meet the IoZ: our Internet of Zombie things appeared first on The Security Ledger with Paul F. Roberts. Related Stories CES Overlooks New Report That Finds Auto Cyber Is A Dumpster Fire The Future of IoT Security Standards IoCs vs.
Let's personalize your content