Jailbreaking LLMs with ASCII Art
Schneier on Security
MARCH 12, 2024
Researchers have demonstrated that putting words in ASCII art can cause LLMs—GPT-3.5, GPT-4 , Gemini, Claude, and Llama2—to ignore their safety instructions. Research paper.

Schneier on Security
MARCH 12, 2024
Researchers have demonstrated that putting words in ASCII art can cause LLMs—GPT-3.5, GPT-4 , Gemini, Claude, and Llama2—to ignore their safety instructions. Research paper.

Troy Hunt
MARCH 12, 2024
Over the last 6 years, we've been very happy to welcome dozens of national governments to have unhindered access to their domains in Have I Been Pwned , free from cost and manual verification barriers. Today, we're happy to welcome Liechtenstein's National Cyber Security Unit who now have full access to their government domains. We provide this support to governments to help those tasked with protecting their national interests understand more about the threats posed by data breac
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MARCH 12, 2024
Information is the lifeblood of the business. Without it, employees can’t work, customers can’t interact with the business, bills can’t be paid and profits can’t be earned. Any given technological environment is useless if its main purpose for existence — the processing and sharing of information — is threatened or eliminated.

Jane Frankland
MARCH 12, 2024
In the tapestry of human interactions, the words ‘kind’ and ‘nice’ are often woven together so tightly that their distinct threads seem indistinguishable. On the surface, both suggest a pleasantness, a quality of being agreeable or gentle in nature. But is there more to it? Could these two seemingly synonymous words actually spell out different narratives in the screenplay of our lives?

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
MARCH 12, 2024
The reassignment of existing equipment takes place when employees leave the organization or receive new computers, mobile devices, printers and other assets. It is essential to follow strict guidelines for equipment reassignment so that company investments, data and privacy are protected. The following checklist, written by Scott Matteson for TechRepublic Premium, will help ensure that.

WIRED Threat Level
MARCH 12, 2024
A closed-door presentation for House lawmakers late last year portrayed American anti-war protesters as having possible ties to Hamas in an effort to kill privacy reforms to a major US spy program.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Penetration Testing
MARCH 12, 2024
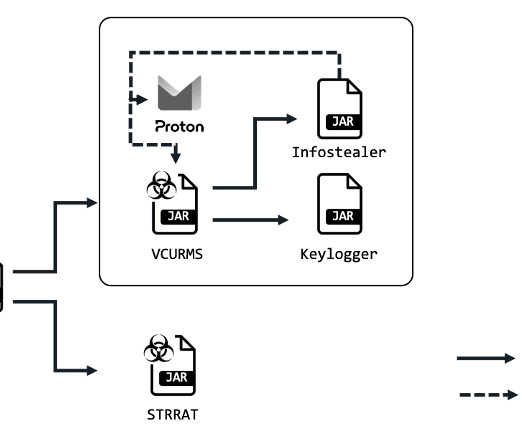
A recently uncovered phishing campaign demonstrates a concerning level of sophistication in its efforts to infiltrate systems and deploy an array of powerful Remote Access Trojans (RATs). Security researchers at FortiGuard Labs have discovered... The post VCURMS: New Java RATs Unleashed in Sophisticated Phishing Scheme appeared first on Penetration Testing.

Bleeping Computer
MARCH 12, 2024
The Tor Project officially introduced WebTunnel, a new bridge type specifically designed to help bypass censorship targeting the Tor network by hiding connections in plain sight. [.

SecureList
MARCH 12, 2024
To help companies with navigating the world of web application vulnerabilities and securing their own web applications, the Open Web Application Security Project (OWASP) online community created the OWASP Top Ten. As we followed their rankings, we noticed that the way we ranked major vulnerabilities was different. Being curious, we decided to find out just how big the difference was.

Penetration Testing
MARCH 12, 2024
Fortinet, a leading cybersecurity firm, has released five security advisories addressing six major vulnerabilities affecting its popular FortiOS, FortiProxy, and FortiClientEMS products. These vulnerabilities have high severity ratings and require immediate attention from administrators... The post Fortinet Issues Urgent Security Patches for Critical Vulnerabilities appeared first on Penetration Testing.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Hacker News
MARCH 12, 2024
Microsoft on Tuesday released its monthly security update, addressing 61 different security flaws spanning its software, including two critical issues impacting Windows Hyper-V that could lead to denial-of-service (DoS) and remote code execution. Of the 61 vulnerabilities, two are rated Critical, 58 are rated Important, and one is rated Low in severity.

Security Affairs
MARCH 12, 2024
Threat actors can abuse QR codes to carry out sophisticated scams, as reported by the Italian Postal Police in its recent alert. As is well known, QR codes are two-dimensional barcodes that can be read with a smartphone or other hand-held device. They are widely used to access information, services, or online payments quickly and conveniently. However, they can also hide scams, as denounced by the Italian Postal Police in its recent alert.
The Hacker News
MARCH 12, 2024
A new malware campaign is leveraging a high-severity security flaw in the Popup Builder plugin for WordPress to inject malicious JavaScript code. According to Sucuri, the campaign has infected more than 3,900 sites over the past three weeks.

Security Affairs
MARCH 12, 2024
Microsoft Patch Tuesday security updates for March 2024 addressed 59 security vulnerabilities in its products, including RCE flaws. Microsoft released Patch Tuesday security updates for March 2023 that address 59 security vulnerabilities in its products. The IT giant addressed vulnerabilities in Microsoft Windows and Windows Components; Office and Office Components; Azure; NET Framework and Visual Studio; SQL Server; Windows Hyper-V; Skype; Microsoft Components for Android; and Microsoft Dynamic

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Bleeping Computer
MARCH 12, 2024
GitHub users accidentally exposed 12.8 million authentication and sensitive secrets in over 3 million public repositories during 2023, with the vast majority remaining valid after five days. [.

Security Boulevard
MARCH 12, 2024
IntroductionZscaler’s ThreatLabz recently discovered a new campaign distributing an infostealer called Tweaks (aka Tweaker) that targets Roblox users. Attackers are exploiting popular platforms, like YouTube and Discord, to distribute Tweaks to Roblox users, capitalizing on the ability of legitimate platforms to evade detection by web filter block lists that typically block known malicious servers.

Security Affairs
MARCH 12, 2024
Russian authorities have detained a South Korean national on cyber espionage charges, it is the first time for a Korean citizen. Russian authorities have arrested a South Korean citizen on charges of cyber espionage, marking the first instance involving a Korean national. “During the investigation of an espionage case, a South Korean citizen Baek Won-soon was identified and detained in Vladivostok, and put into custody under a court order.

Bleeping Computer
MARCH 12, 2024
Today is Microsoft's March 2024 Patch Tuesday, and security updates have been released for 60 vulnerabilities, including eighteen remote code execution flaws. [.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Malwarebytes
MARCH 12, 2024
February was a particularly busy month for search-based malvertising with the number of incidents we documented almost doubling. We saw similar payloads being dropped but also a few new ones that were particularly good at evading detection. One malware family we have been tracking on this blog is FakeBat. It is very unique in that the threat actor uses MSIX installers packaged with heavily obfuscated PowerShell code.

Bleeping Computer
MARCH 12, 2024
The KB5035849 cumulative update released during today's Patch Tuesday fails to install on Windows 10 and Windows Server systems with 0xd0000034 errors. [.

Penetration Testing
MARCH 12, 2024
Security researchers Quynh Le and Eng De Sheng from Ensign InfoSecurity Labs have uncovered a major security flaw (CVE-2024-25331) in the popular D-Link DIR-822 router. This vulnerability leaves the door wide open for unauthenticated... The post No More Patches: D-Link DIR-822 Vulnerable to Remote Takeovers (CVE-2024-25331) appeared first on Penetration Testing.

The Hacker News
MARCH 12, 2024
Threat hunters have discovered a set of seven packages on the Python Package Index (PyPI) repository that are designed to steal BIP39 mnemonic phrases used for recovering private keys of a cryptocurrency wallet. The software supply chain attack campaign has been codenamed BIPClip by ReversingLabs.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
MARCH 12, 2024
Carbon Black’s uncertain future following the closing of Broadcom’s $69 billion acquisition of VMware in November is now settled, with the security software business merging with Symantec to form Broadcom’s new Enterprise Security Group. Broadcom will make “significant investments in both brands” and offer both Carbon Black and Symantec product portfolios through the new business.

We Live Security
MARCH 12, 2024
What cyberthreats could wreak havoc on elections this year and how worried should we as voters be about the integrity of our voting systems?

Penetration Testing
MARCH 12, 2024
Enterprise software leader SAP released a critical set of patches as part of its March 2024 Security Patch Day, addressing multiple severe vulnerabilities within its widely used product suite. Topping the list are three... The post SAP Security Patch Day: CVE-2024-22127 – Critical Vulnerability Demand Immediate Action appeared first on Penetration Testing.

Security Boulevard
MARCH 12, 2024
In recent months, a concerning trend has emerged within the healthcare sector: the resurgence of BlackCat ransomware attacks. The BlackCat ransomware healthcare attack has prompted a joint advisory from the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS), warning healthcare organizations about […] The post Alert: FBI Warns Of BlackCat Ransomware Healthcare Attack appeared first on TuxCare.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
The Hacker News
MARCH 12, 2024
In a world of ever-expanding jargon, adding another FLA (Four-Letter Acronym) to your glossary might seem like the last thing you’d want to do.

Bleeping Computer
MARCH 12, 2024
Microsoft has released the KB5035845 cumulative update for Windows 10 21H2 and Windows 10 22H2, which includes nine new changes and fixes. [.

SecureWorld News
MARCH 12, 2024
Discovering your WordPress site has been compromised is a daunting experience for any website owner. This situation demands immediate action to mitigate damage and restore security. WordPress is an exceptionally popular content management system (CMS). According to recent statistics, WordPress controls 62.5% of the CMS market share , with 42.7% of all sites using WordPress.

Penetration Testing
MARCH 12, 2024
Researchers from Vrije Universiteit Amsterdam and IBM Research Europe have uncovered a new security vulnerability dubbed “GhostRace” (CVE-2024-2193) that exposes a critical flaw in the foundational elements of operating system security: synchronization primitives. This... The post GhostRace (CVE-2024-2193): Processor Flaws Enable Kernel Attacks appeared first on Penetration Testing.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content