Why Are Meat Companies Being Targeted By Hackers: A Conversation With Kennedy
Joseph Steinberg
JUNE 3, 2021
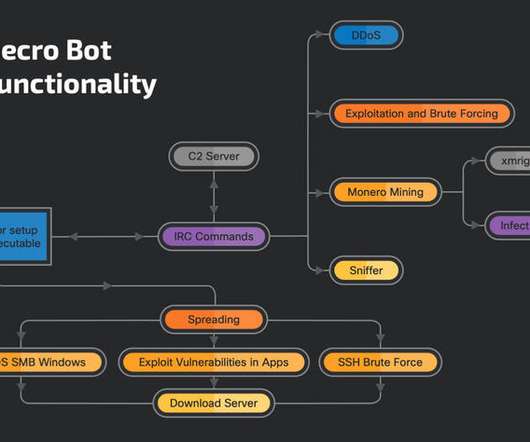
Joseph Steinberg recently discussed with Fox Business Network host and commentator, Kennedy, why hackers are targeting meat companies, pipelines, and other important elements of the US economy’s supply chain… and, what can Americans do to stop such attacks. To listen to the discussion, please either utilize the embedded player below, or click the image underneath it.









































Let's personalize your content