The Power of Storytelling in Risk Management
Speaker: Dr. Karen Hardy, CEO and Chief Risk Officer of Strategic Leadership Advisors LLC
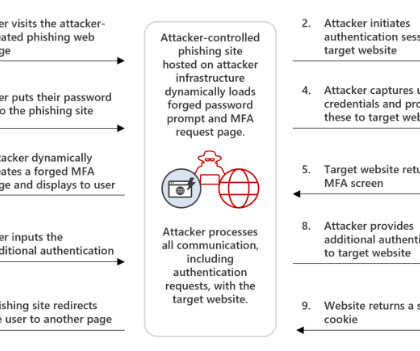
Communication is a core component of a resilient organization's risk management framework. However, risk communication involves more than just reporting information and populating dashboards, and we may be limiting our skillset. Storytelling is the ability to express ideas and convey messages to others, including stakeholders. When done effectively, it can help interpret complex risk environments for leaders and inform their decision-making.




























Let's personalize your content