5 most dangerous new attack techniques
CSO Magazine
APRIL 27, 2023
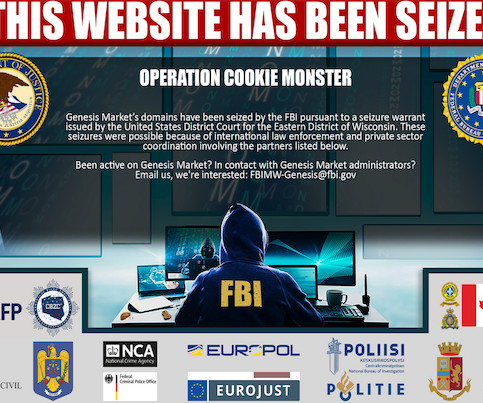
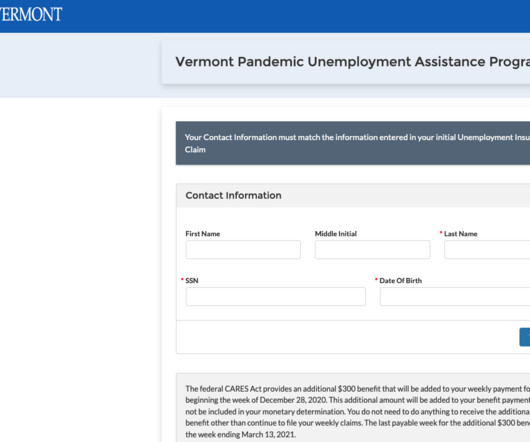
Cyber experts from the SANS Institute have revealed the five most dangerous new attack techniques being used by attackers including cyber criminals and nation-state actors. They were presented in a session at the RSA Conference in San Francisco, where a panel of SANS analysts explored emerging Tactics, Techniques, and Procedures (TTPs) and advised organizations on how to prepare for them.














Let's personalize your content