Cyber Warfare Lessons From the Russia-Ukraine Conflict
Dark Reading
MAY 22, 2023
Techniques used in cyber warfare can be sold to anyone — irrespective of borders, authorities, or affiliations. We need to develop strategies to respond at scale.

Dark Reading
MAY 22, 2023
Techniques used in cyber warfare can be sold to anyone — irrespective of borders, authorities, or affiliations. We need to develop strategies to respond at scale.

Schneier on Security
MAY 25, 2023
Interesting essay on the poisoning of LLMs—ChatGPT in particular: Given that we’ve known about model poisoning for years, and given the strong incentives the black-hat SEO crowd has to manipulate results, it’s entirely possible that bad actors have been poisoning ChatGPT for months. We don’t know because OpenAI doesn’t talk about their processes, how they validate the prompts they use for training, how they vet their training data set, or how they fine-tune ChatGPT.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
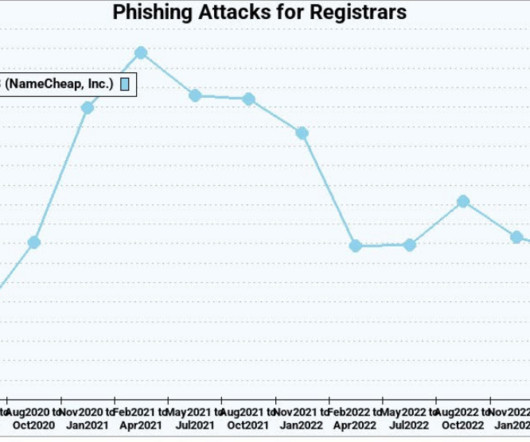
Krebs on Security
MAY 26, 2023
The number of phishing websites tied to domain name registrar Freenom dropped precipitously in the months surrounding a recent lawsuit from social networking giant Meta , which alleged the free domain name provider has a long history of ignoring abuse complaints about phishing websites while monetizing traffic to those abusive domains. The volume of phishing websites registered through Freenom dropped considerably since the registrar was sued by Meta.

Tech Republic Security
MAY 23, 2023
Generative AI is of particular interest to leaders for the benefits of cost savings, efficiency and effectiveness. The post EY survey: Tech leaders to invest in AI, 5G, cybersecurity, big data, metaverse appeared first on TechRepublic.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Bleeping Computer
MAY 21, 2023
Researchers at Tencent Labs and Zhejiang University have presented a new attack called 'BrutePrint,' which brute-forces fingerprints on modern smartphones to bypass user authentication and take control of the device. [.

Schneier on Security
MAY 23, 2023
In case you don’t have enough to worry about, someone has built a credible handwriting machine: This is still a work in progress, but the project seeks to solve one of the biggest problems with other homework machines, such as this one that I covered a few months ago after it blew up on social media. The problem with most homework machines is that they’re too perfect.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
MAY 22, 2023
A new Linux Foundation report finds that the global focus is on cloud/containers, cybersecurity and AI/ML skills, and that upskilling is key. The post Report: More organizations still plan to increase their tech staff appeared first on TechRepublic.

Trend Micro
MAY 22, 2023
In this blog entry, we will examine the security risks related to file extension-related Top-Level Domains (TLDs) while also providing best practices and recommendations on how both individual users and organizations can protect themselves from these hazards.

Schneier on Security
MAY 22, 2023
Google has backtracked on its plan to delete inactive YouTube videos—at least for now. Of course, it could change its mind anytime it wants. It would be nice if this would get people to think about the vulnerabilities inherent in letting a for-profit monopoly decide what of human creativity is worth saving.

Bleeping Computer
MAY 24, 2023
Ongoing attacks are targeting an Unauthenticated Stored Cross-Site Scripting (XSS) vulnerability in a WordPress cookie consent plugin named Beautiful Cookie Consent Banner with more than 40,000 active installs. [.

Speaker: Speakers:
In today's digital age, having an untrained workforce can be a significant risk to your business. Cyber threats are evolving; without proper training, your employees could be the weakest link in your defense. This webinar empowers leaders like you with the tools and strategies needed to transform your employees into a robust frontline defense against cyber attacks.

Tech Republic Security
MAY 24, 2023
Barracuda Networks found that spearphishing exploits last year worked to great effect and took days to detect. The post Spearphishing report: 50% of companies were impacted in 2022 appeared first on TechRepublic.

WIRED Threat Level
MAY 22, 2023
In response to an EU proposal to scan private messages for illegal material, the country's officials said it is “imperative that we have access to the data.

Schneier on Security
MAY 24, 2023
It’s been a big month for US data privacy. Indiana, Iowa, and Tennessee all passed state privacy laws, bringing the total number of states with a privacy law up to eight. No private right of action in any of those, which means it’s up to the states to enforce the laws.

Bleeping Computer
MAY 24, 2023
GitLab has released an emergency security update, version 16.0.1, to address a maximum severity (CVSS v3.1 score: 10.0) path traversal flaw tracked as CVE-2023-2825. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
MAY 25, 2023
Microsoft published specifics on the Volt Typhoon state-aligned China actor. Experts say raising awareness of threats is critical. The post Microsoft warns of Volt Typhoon, latest salvo in global cyberwar appeared first on TechRepublic.

WIRED Threat Level
MAY 20, 2023
From USB worms to satellite-based hacking, Russia’s FSB hackers, known as Turla, have spent 25 years distinguishing themselves as “adversary number one.

Schneier on Security
MAY 26, 2023
Cyberspace operations now officially has a physical dimension, meaning that the United States has official military doctrine about cyberattacks that also involve an actual human gaining physical access to a piece of computing infrastructure. A revised version of Joint Publication 3-12 Cyberspace Operations—published in December 2022 and while unclassified, is only available to those with DoD common access cards, according to a Joint Staff spokesperson—officially provides a definition

Bleeping Computer
MAY 24, 2023
Microsoft says a Chinese cyberespionage group it tracks as Volt Typhoon has been targeting critical infrastructure organizations across the United States, including Guam, since at least mid-2021. [.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
MAY 25, 2023
The GDPR, in effect for five years on May 25, has influenced the U.S. data privacy laws and is likely to exert itself when AI creates a new set of privacy challenges. The post Experts laud GDPR at five year milestone appeared first on TechRepublic.

Security Boulevard
MAY 26, 2023
Shouty name—dangerous game. Red-team tool ripe for misuse. The post COSMICENERGY: ‘Russian’ Threat to Power Grids ICS/OT appeared first on Security Boulevard.

Google Security
MAY 26, 2023
Vincent Winstead, Technical Program Manager It’s Google CTF time! Get your hacking toolbox ready and prepare your caffeine for rapid intake. The competition kicks off on June 23 2023 6:00 PM UTC and runs through June 25 2023 6:00 PM UTC. Registration is now open at g.co/ctf. Google CTF gives you a chance to challenge your skillz, show off your hacktastic abilities, and learn some new tricks along the way.

Bleeping Computer
MAY 24, 2023
A new PowerShell-based malware dubbed PowerExchange was used in attacks linked to APT34 Iranian state hackers to backdoor on-premise Microsoft Exchange servers. [.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.

Tech Republic Security
MAY 23, 2023
On-premises artificial intelligence and specifically trained generative AI are now enterprise trends. Leaders from Dell and NVIDIA and analysts from Forrester Research weigh in. The post Dell’s Project Helix heralds a move toward specifically trained generative AI appeared first on TechRepublic.

CSO Magazine
MAY 23, 2023
Like most CSOs, Joe Sullivan was drawn to the role to help prevent cybercrimes. His role as CSO of Uber was something of a shift from his previous job prosecuting cybercriminals as an assistant US attorney, but closer to the tip of the cybersecurity spear. As a top-level professional in the business of defending against the bad guys, it was unexpected and not a little ironic that he would find himself on the other side of the justice system.

Trend Micro
MAY 25, 2023
This is an analysis of Bandit Stealer, a new Go-based information-stealing malware capable of evading detection as it targets multiple browsers and cryptocurrency wallets.

Bleeping Computer
MAY 26, 2023
Swiss tech multinational and U.S. government contractor ABB has confirmed that some of its systems were impacted by a ransomware attack, previously described by the company as "an IT security incident." [.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Tech Republic Security
MAY 22, 2023
With NordLocker, you can store, manage and share individual files. Learn how with this step-by-step guide. The post How to manage and share files online using NordLocker appeared first on TechRepublic.

The Hacker News
MAY 26, 2023
Security researchers have shared a deep dive into the commercial Android spyware called Predator, which is marketed by the Israeli company Intellexa (previously Cytrox). Predator was first documented by Google's Threat Analysis Group (TAG) in May 2022 as part of attacks leveraging five different zero-day flaws in the Chrome web browser and Android.

We Live Security
MAY 25, 2023
ESET researchers reveal details about a prevalent cryptor, operating as a cryptor-as-a-service used by tens of malware families The post Shedding light on AceCryptor and its operation appeared first on WeLiveSecurity

CSO Magazine
MAY 22, 2023
Cybersecurity activity around business email compromise (BEC) spiked between April 2022 and April 2023, with over 150,000 daily attempts, on average, detected by the Microsoft Microsoft’s Digital Crimes Unit (DCU). The findings were highlighted in the latest edition of Microsoft’s Cyber Signals , a cyberthreat intelligence report that spotlights security trends and insights gathered from Microsoft’s 43 trillion security signals and 8,500 security experts.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Let's personalize your content