ChatGPT: Hopes, Dreams, Cheating and Cybersecurity
Lohrman on Security
JANUARY 29, 2023
ChatGPT is an AI-powered chatbot created by OpenAI. So what are the opportunities and risks with using this technology across different domains?

Lohrman on Security
JANUARY 29, 2023
ChatGPT is an AI-powered chatbot created by OpenAI. So what are the opportunities and risks with using this technology across different domains?

Schneier on Security
JANUARY 3, 2023
A group of Chinese researchers have just published a paper claiming that they can—although they have not yet done so—break 2048-bit RSA. This is something to take seriously. It might not be correct, but it’s not obviously wrong. We have long known from Shor’s algorithm that factoring with a quantum computer is easy. But it takes a big quantum computer, on the orders of millions of qbits, to factor anything resembling the key sizes we use today.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
JANUARY 9, 2023
Identity thieves have been exploiting a glaring security weakness in the website of Experian , one of the big three consumer credit reporting bureaus. Normally, Experian requires that those seeking a copy of their credit report successfully answer several multiple choice questions about their financial history. But until the end of 2022, Experian’s website allowed anyone to bypass these questions and go straight to the consumer’s report.

Tech Republic Security
JANUARY 24, 2023
The criminals took advantage of an API to grab personal details such as customer names, billing addresses, email addresses, phone numbers, dates of birth, and T-Mobile account numbers. The post How hackers stole the personal data of 37 million T-Mobile customers appeared first on TechRepublic.

Speaker: Speakers:
In today's digital age, having an untrained workforce can be a significant risk to your business. Cyber threats are evolving; without proper training, your employees could be the weakest link in your defense. This webinar empowers leaders like you with the tools and strategies needed to transform your employees into a robust frontline defense against cyber attacks.

Bleeping Computer
JANUARY 27, 2023
Microsoft says this week's five-hour-long Microsoft 365 worldwide outage was caused by a router IP address change that led to packet forwarding issues between all other routers in its Wide Area Network (WAN). [.

We Live Security
JANUARY 27, 2023
Sandworm continues to conduct attacks against carefully chosen targets in the war-torn country The post SwiftSlicer: New destructive wiper malware strikes Ukraine appeared first on WeLiveSecurity
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Schneier on Security
JANUARY 17, 2023
No details , though: According to the complaint against him, Al-Azhari allegedly visited a dark web site that hosts “unofficial propaganda and photographs related to ISIS” multiple times on May 14, 2019. In virtue of being a dark web site—that is, one hosted on the Tor anonymity network—it should have been difficult for the site owner’s or a third party to determine the real IP address of any of the site’s visitors.

Krebs on Security
JANUARY 19, 2023
T-Mobile today disclosed a data breach affecting tens of millions of customer accounts, its second major data exposure in as many years. In a filing with federal regulators, T-Mobile said an investigation determined that someone abused its systems to harvest subscriber data tied to approximately 37 million current customer accounts. Image: customink.com In a filing today with the U.S.

Tech Republic Security
JANUARY 27, 2023
Working with international law enforcement, the FBI said it has seized control of the servers the Hive group uses to communicate with members. The post FBI takes down Hive ransomware group appeared first on TechRepublic.

Quick Heal Antivirus
JANUARY 25, 2023
As cyber threats continue to evolve and become more sophisticated, it’s crucial for security researchers and professionals. The post AsyncRAT Analysis with ChatGPT appeared first on Quick Heal Blog | Latest computer security news, tips, and advice.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
JANUARY 13, 2023
Microsoft has addressed a false positive triggered by a buggy Microsoft Defender ASR rule that would delete application shortcuts from the desktop, the Start menu, and the taskbar and, in some cases, render existing shortcuts unusable as they couldn't be used to launch the linked apps. [.].

Security Boulevard
JANUARY 13, 2023
Linanto’s popular web hosting control panel, CWP, has a nasty flaw. It’s easily exploitable—in fact, it’s being exploited RIGHT NOW. The post Yikes, Control Web Panel has Critical RCE — Patch NOW appeared first on Security Boulevard.

Schneier on Security
JANUARY 27, 2023
Early in his career, Kevin Mitnick successfully hacked California law. He told me the story when he heard about my new book , which he partially recounts his 2012 book, Ghost in the Wires. The setup is that he just discovered that there’s warrant for his arrest by the California Youth Authority, and he’s trying to figure out if there’s any way out of it.
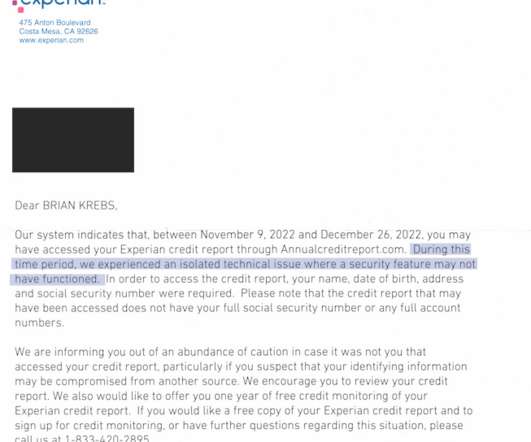
Krebs on Security
JANUARY 25, 2023
On Dec. 23, 2022, KrebsOnSecurity alerted big-three consumer credit reporting bureau Experian that identity thieves had worked out how to bypass its security and access any consumer’s full credit report — armed with nothing more than a person’s name, address, date of birth, and Social Security number. Experian fixed the glitch, but remained silent about the incident for a month.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
JANUARY 4, 2023
A nightly build version of a machine-learning framework dependency has been compromised. The package ran malicious code on affected systems and stole data from unsuspecting users. The post Machine-Learning Python package compromised in supply chain attack appeared first on TechRepublic.

eSecurity Planet
JANUARY 5, 2023
After a year that saw massive ransomware attacks and open cyber warfare, the biggest question in cybersecurity for 2023 will likely be how much of those attack techniques get commoditized and weaponized. “In 2022, governments fought wars online, businesses were affected by multiple ransomware gangs, and regular users’ data was constantly on hackers’ radars,” said NordVPN CTO Marijus Briedis. 2023, he predicted, “will not be any easier when it comes to keeping users’

Bleeping Computer
JANUARY 14, 2023
Brave Browser version 1.47 was released yesterday, adding the Snowflake extension in the software's settings, enabling users to turn their devices into proxies that help users in censored countries connect to Tor. [.].

Security Boulevard
JANUARY 20, 2023
The Un-carrier is In-secure, it seems. Un-believable. In-credibly in-competent. CEO Mike Sievert (pictured) might become un-CEO. The post T-Mobile’s SIXTH Breach in 5 years: 37M Users’ PII Leaks appeared first on Security Boulevard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Schneier on Security
JANUARY 20, 2023
From an article about Zheng Xiaoqing, an American convicted of spying for China: According to a Department of Justice (DOJ) indictment, the US citizen hid confidential files stolen from his employers in the binary code of a digital photograph of a sunset, which Mr Zheng then mailed to himself.

We Live Security
JANUARY 10, 2023
ESET researchers identified an active StrongPity campaign distributing a trojanized version of the Android Telegram app, presented as the Shagle app – a video-chat service that has no app version. The post StrongPity espionage campaign targeting Android users appeared first on WeLiveSecurity.

Tech Republic Security
JANUARY 19, 2023
The cybersecurity implications of ChatGPT are vast, especially for email exploits, but putting up guardrails, flagging elements of phishing emails that it doesn’t touch and using it to train itself could help boost defense. The post As a cybersecurity blade, ChatGPT can cut both ways appeared first on TechRepublic.

eSecurity Planet
JANUARY 20, 2023
CyberArk researchers are warning that OpenAI’s popular new AI tool ChatGPT can be used to create polymorphic malware. “[ChatGPT]’s impressive features offer fast and intuitive code examples, which are incredibly beneficial for anyone in the software business,” CyberArk researchers Eran Shimony and Omer Tsarfati wrote this week in a blog post that was itself apparently written by AI. “However, we find that its ability to write sophisticated malware that holds no mali

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Bleeping Computer
JANUARY 4, 2023
A data leak described as containing email addresses for over 200 million Twitter users has been published on a popular hacker forum for about $2. BleepingComputer has confirmed the validity of many of the email addresses listed in the leak. [.].

Security Boulevard
JANUARY 27, 2023
The Federal Trade Commission (FTC) chair, Lina M. Khan, recently announced the commission’s intent to adjust a rule that would prohibit non-compete agreements by workers or independent contractors. Their rationale? Unfair competition—which, therefore, falls under the purview of the FTC. This could have a huge impact on the cybersecurity and IT industries, and open up.

Schneier on Security
JANUARY 19, 2023
A group of Swiss researchers have published an impressive security analysis of Threema. We provide an extensive cryptographic analysis of Threema, a Swiss-based encrypted messaging application with more than 10 million users and 7000 corporate customers. We present seven different attacks against the protocol in three different threat models. As one example, we present a cross-protocol attack which breaks authentication in Threema and which exploits the lack of proper key separation between diff

CyberSecurity Insiders
JANUARY 16, 2023
First, is the news that the Indian government has launched its own Mobile Operating systems that have capabilities to take on international rivals like iOS and Android. Within the next few weeks, the government of the sub-continent is preparing to release an indigenous mobile operating system that has the potential to offer a health competition to American technology giants and will be safe to use in the current cyber threat landscape.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Tech Republic Security
JANUARY 6, 2023
A spate of zero-day exploits against Twitter, Rackspace and others late last year showed the limits of a cybersecurity workforce under duress, a step behind and understaffed with some 3.4 million vacant seats. The post Recent 2022 cyberattacks presage a rocky 2023 appeared first on TechRepublic.

Trend Micro
JANUARY 23, 2023
In this blog entry, we’d like to highlight our findings on Vice Society, which includes an end-to-end infection diagram that we were able to create using Trend Micro internal telemetry.

Bleeping Computer
JANUARY 26, 2023
Microsoft urged customers today to keep their on-premises Exchange servers patched by applying the latest supported Cumulative Update (CU) to have them always ready to deploy an emergency security update. [.

Security Boulevard
JANUARY 2, 2023
In the fintech industry, Cloud Computing has emerged as a new trend that has greatly impacted the needs of the financial sector and given it a huge potential to expand. Fintech is predicted to have a $124.3 billion global market by the end of 2025, with a compound annual growth rate of 23.84%. So why […]. The post How Cloud Computing Affects Fintech?

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content