US Orders Rare Emergency System Shut-Downs After Severe CyberSecurity Breach Hits Government And Businesses
Joseph Steinberg
DECEMBER 14, 2020
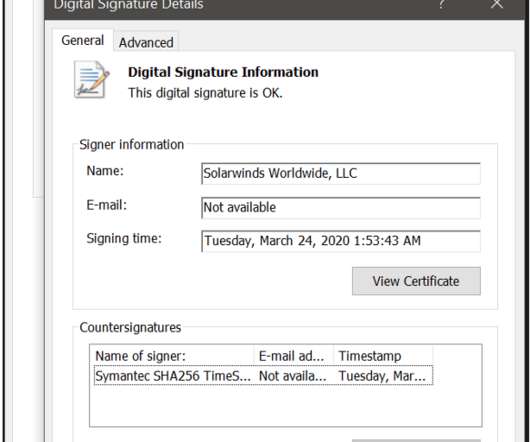
The U.S. government instructed all of its civilian agencies to immediately shut off various popular network and system management products being exploited as part of an ongoing cyberattack. Russian government hackers are believed to have poisoned with malware updates of the SolarWinds Orion products used in many government agencies and in over 80% of the Fortune 500, introducing vulnerabilities that the hackers then exploited to conduct espionage and to pilfer extremely sensitive materials.










































Let's personalize your content