Weekly Update 340
Troy Hunt
MARCH 25, 2023
I'm excited about coming to Prague. One more country to check off the list, apparently a beautiful city and perhaps what I'm most stoked about, it's the home of Prusa 3D. Writing this as I wrangle prints out of my trusty MK3S+, I'm going to do my best to catch up with folks there and see some of the super cool stuff they're doing.










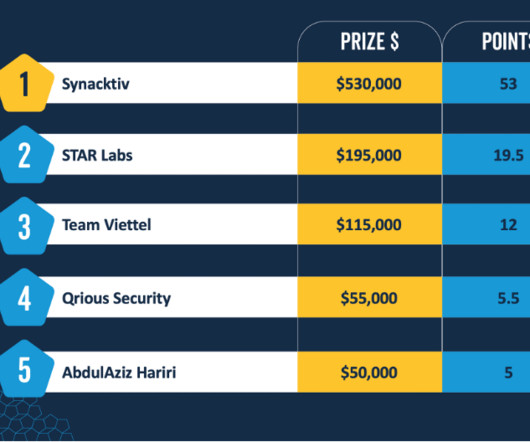

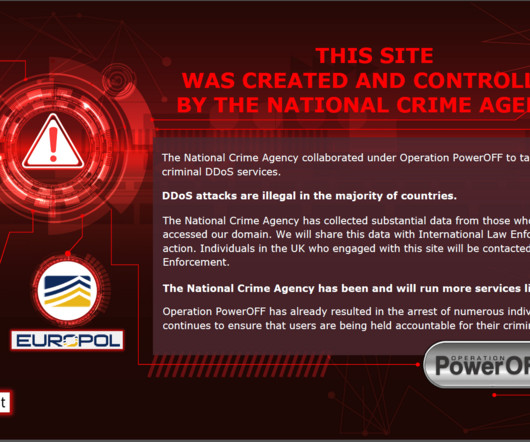












Let's personalize your content