ChatGPT-Written Malware
Schneier on Security
JANUARY 10, 2023
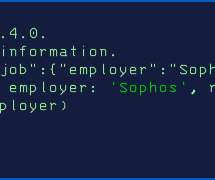
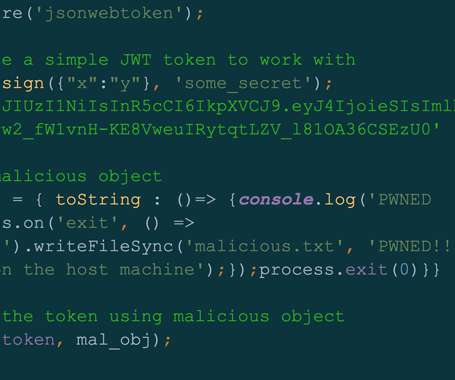
I don’t know how much of a thing this will end up being, but we are seeing ChatGPT-written malware in the wild. …within a few weeks of ChatGPT going live, participants in cybercrime forums—some with little or no coding experience—were using it to write software and emails that could be used for espionage, ransomware, malicious spam, and other malicious tasks. “It’s still too early to decide whether or not ChatGPT capabilities will become the new favorite tool for








































Let's personalize your content