FBI’s Vetted Info Sharing Network ‘InfraGard’ Hacked
Krebs on Security
DECEMBER 13, 2022
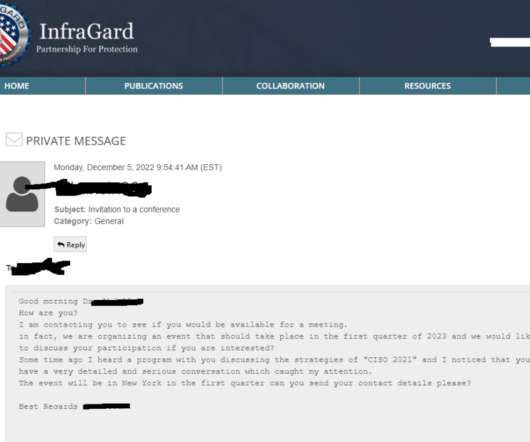
InfraGard , a program run by the U.S.
Krebs on Security
DECEMBER 13, 2022
InfraGard , a program run by the U.S.

Tech Republic Security
DECEMBER 13, 2022
No longer limited to email, BEC attacks are hitting users through text messages in an attempt to steal money or commit other types of fraud, says Trustwave. The post Business email compromise attacks now targeting people via SMS messages appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
DECEMBER 13, 2022
Here's what you need to patch now, including six critical updates for Microsoft's final Patch Tuesday of the year
Tech Republic Security
DECEMBER 13, 2022
From safety to where? Find out the right way to turn with this comprehensive analysis of seven options for your business. The post Top industrial IoT security solutions appeared first on TechRepublic.
Speaker: William Hord, Vice President of ERM Services
Join us as we discuss the various tangents of data and the change management process that will help you make better risk-based business decisions to save time and money for your organization.

Dark Reading
DECEMBER 13, 2022
Threat actors leak employee email addresses, corporate reports, and IT asset information on a hacker forum after an attack on an Uber technology partner

Security Affairs
DECEMBER 13, 2022
A new Python backdoor is targeting VMware ESXi servers, allowing attackers to take over compromised systems. Juniper Networks researchers spotted a previously undocumented Python backdoor targeting VMware ESXi servers.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

CyberSecurity Insiders
DECEMBER 13, 2022
Central government employees of India will receive a Standard Operating Procedure (SOP) on Cyber Attacks by this month and suggesting measures to take before a cyber attack and steps to mitigate risks, if in case, an organization becomes a victim to a digital attack.

Security Affairs
DECEMBER 13, 2022
VMware fixed three flaws in multiple products, including a virtual machine escape issue exploited at the GeekPwn 2022 hacking competition.

Dark Reading
DECEMBER 13, 2022
Organizations need servant leaders to step forward and make their teams' professional effectiveness and happiness a priority

Security Affairs
DECEMBER 13, 2022
Citrix urges customers to update their installs to fix actively exploited zero-day (CVE-2022-27518) in Citrix ADC and Gateway. Citrix urges administrators to apply security updates for a zero-day vulnerability, tracked as CVE-2022-27518, in Citrix ADC and Gateway.

Speaker: Ronald Eddings, Cybersecurity Expert and Podcaster
In this webinar, Ronald Eddings, Cybersecurity Expert, will outline the relationship between SaaS apps and IT & security teams, along with several actionable solutions to overcome the new difficulties facing your organization.
Dark Reading
DECEMBER 13, 2022
Citrix issues a critical update as NSA warns that the APT5 threat group is actively trying to target ADC environments

Naked Security
DECEMBER 13, 2022
There's an update for everything this time, not just for iOS. Apple Vulnerability CVE-2022-42856

Dark Reading
DECEMBER 13, 2022
Deloitte's Future of Cyber study highlights the fact that cybersecurity is an essential part of business success and should not be limited to just mitigating IT risks

WIRED Threat Level
DECEMBER 13, 2022
The suit claims the company lacks adequate moderation to prevent widespread hate speech that has led to violence and death. Business Business / Social Media Security / National Security

Speaker: Karl Camilleri, Cloud Services Product Manager at phoenixNAP
Through a detailed analysis of major attacks and their consequences, Karl Camilleri, Cloud Services Product Manager at phoenixNAP, will discuss the state of ransomware and future predictions, as well as provide best practices for attack prevention and recovery.

Dark Reading
DECEMBER 13, 2022
Jira, Confluence,Trello, and BitBucket affected

CyberSecurity Insiders
DECEMBER 13, 2022
India’s Corona fighting digital platform COWIN Portal has been reportedly been hacked by a hacker who is ready to sell the access details and some health worker data to interested parties.
Security Affairs
DECEMBER 13, 2022
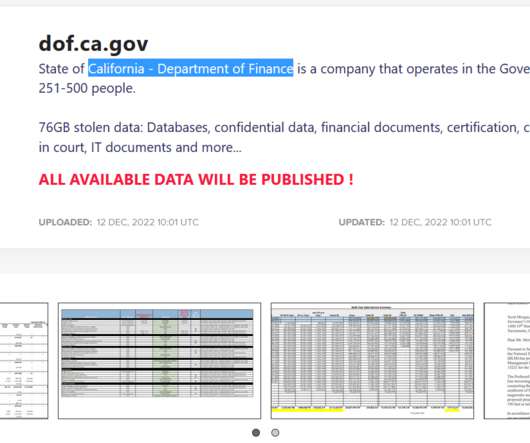
LockBit ransomware gang hacked the California Department of Finance and threatens to leak data stolen from its systems.

CyberSecurity Insiders
DECEMBER 13, 2022
Evil Corp, the internationally acclaimed group of cyber criminals, is back in news for having links to the Silence Group developed new malware called ‘TrueBot’. The malware’s primary motive is to steal money and to launch DDoS attacks.

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance

Dark Reading
DECEMBER 13, 2022
Software teams can now fix bugs faster with faster release cycles, but breach pressure is increasing. Using SBOM and automation will help better detect, prevent, and remediate security issues throughout the software development life cycle

CyberSecurity Insiders
DECEMBER 13, 2022
Day to day a new ransomware emerges on the web giving us a feeling that the threat seems to be a never-ending saga and is going through evolution with time.

Dark Reading
DECEMBER 13, 2022
Offensive security researchers found 63 previously unreported vulnerabilities in printers, phones, and network-attached storage devices in the Zero Day Initiative's latest hackathon

CyberSecurity Insiders
DECEMBER 13, 2022
LockBit, the notorious gang spreading ransomware, has victimized the servers operating in/for the California’s Finance Department, disrupting the services to a certain extent.

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.
Dark Reading
DECEMBER 13, 2022
OSV-Scanner generates a list of dependencies in a project and checks the OSV database for known vulnerabilities, Google says

We Live Security
DECEMBER 13, 2022
Think outside the (gift) box. Here are a few ideas for security and privacy gifts to get for your relatives – or even for yourself. Some don’t cost a penny! The post Top tips for security‑ and privacy‑enhancing holiday gifts appeared first on WeLiveSecurity. Cybersecurity
WIRED Threat Level
DECEMBER 13, 2022
The company has taken measures to mitigate the risks, but security researchers warn of a broader threat. Security Security / Cyberattacks and Hacks Security / Security News

Security Boulevard
DECEMBER 13, 2022
Stop me if you’ve heard this one before: Next year is the year we will finally eliminate passwords. That statement has been a staple of annual cybersecurity predictions for at least a decade, but could 2023 actually be the year that we see a major shift toward the passwordless workplace?

Cisco CSR
DECEMBER 13, 2022
Modernize your firewall for greater security resilience. Cybersecurity has changed dramatically since the dawn of firewalls in the 1980s. But despite all the upheaval and innovation, they have stood the test of time.

Naked Security
DECEMBER 13, 2022
Tales of derring-do in the cyberunderground! And some zero-days.). Microsoft Vulnerability driver signing Exploit Patch Tuesday vulnerability
Security Affairs
DECEMBER 13, 2022
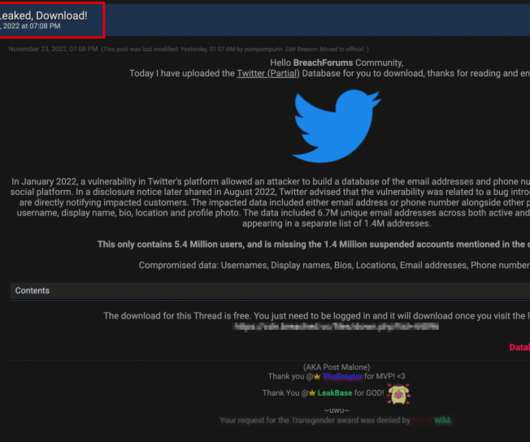
Twitter confirmed that the recent leak of members’ profile information resulted from the 2021 data breach disclosed in August 2022. Twitter confirmed that the recent data leak of millions of profiles resulted from the 2021 data breach that the company disclosed in August 2022.

BH Consulting
DECEMBER 13, 2022
This regulations roundup uncovers how the European Union has been busy laying the groundwork for a world of open data sharing and digital sovereignty. The forthcoming EU Data Act and Data Governance Act aim to make more data available for society and the economy.

WIRED Threat Level
DECEMBER 13, 2022
And new evidence suggests those hackers may have collaborated with the police who investigated him. Security Security / Cyberattacks and Hacks Security / Security News

Security Boulevard
DECEMBER 13, 2022
A recent uptick in the reports of SMS-based business email compromise (BEC) messages may indicate a wider trend that has seen a surge of phishing scams via text messages.
Let's personalize your content