SMS Phishers Harvested Phone Numbers, Shipment Data from UPS Tracking Tool
Krebs on Security
JUNE 22, 2023
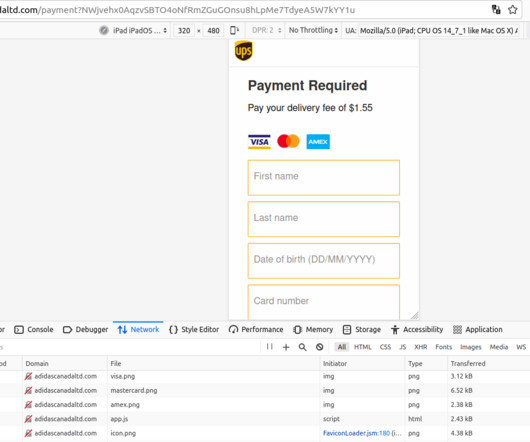
The United Parcel Service (UPS) says fraudsters have been harvesting phone numbers and other information from its online shipment tracking tool in Canada to send highly targeted SMS phishing (a.k.a. “smishing”) messages that spoofed UPS and other top brands. The missives addressed recipients by name, included details about recent orders, and warned that those orders wouldn’t be shipped unless the customer paid an added delivery fee.






































Let's personalize your content