Madonna thinks her computer was hacked
We Live Security
DECEMBER 22, 2014
Turns out that the Material Girl has had her material stolen, and she's blaming hackers!
We Live Security
DECEMBER 22, 2014
Turns out that the Material Girl has had her material stolen, and she's blaming hackers!
NopSec
DECEMBER 4, 2014
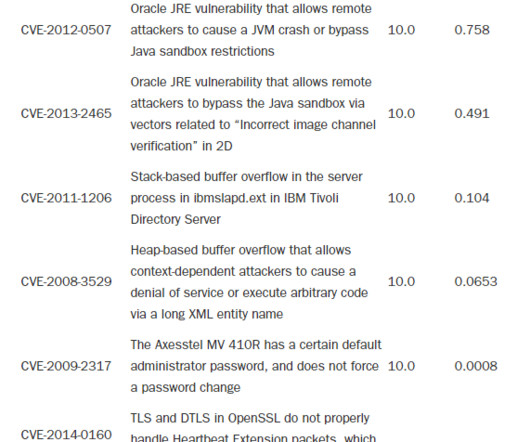
Heartbleed (CVE-2014-0160) is a vulnerability with a CVSSv2 base score of only 5.0/10.0. Though its CVSS score is relatively low, Heartbleed has definitely been one of the most severe security events the Internet has never seen. It is found in the Open SSL cryptographic software library, which is omnipresent on the Internet, and it exploits a buffer over-read weakness in the library, a situation where more data can be read than should be allowed ( [link] ).
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Privacy and Cybersecurity Law
DECEMBER 22, 2014
Earlier this year we told you that Canada’s Anti-Spam Law (CASL) is not just for Canadians. CASL is also not just […].
We Live Security
DECEMBER 22, 2014
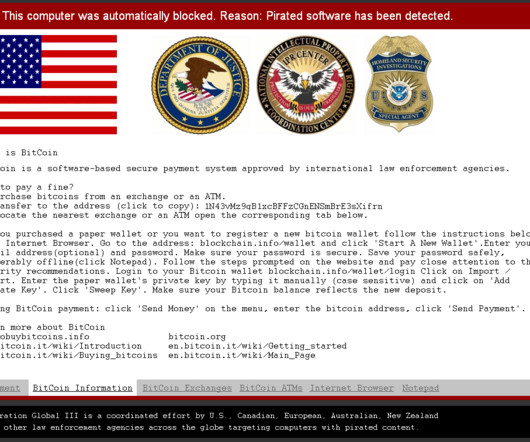
Win32/VirLock is ransomware that locks victims screens but also acts as parasitic virus, infecting existing files on their computers. The virus is also polymorphic, which makes it an interesting piece of malware to analyze. This is the first time such combination of malware features has been observed.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
We Live Security
DECEMBER 18, 2014
As regular readers will know, every year we publish our predictions on cybercrime attacks for the year ahead. Well, our South American research team has spent the last few weeks putting together our predictions for 2015.
We Live Security
DECEMBER 16, 2014
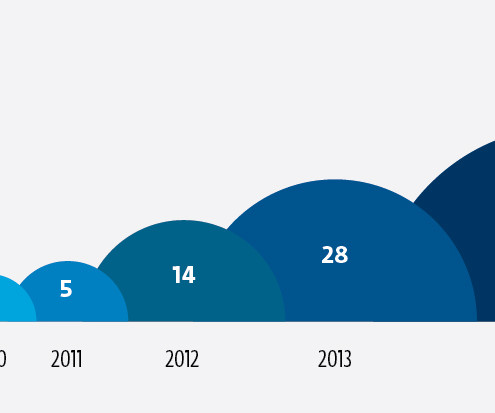
Today, we are publishing research on ransomware that emerged in 2014. We have posted blog articles about this threat before, to raise awareness when we realized the criminals were targeting the United Kingdom and Spain.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

We Live Security
DECEMBER 8, 2014
Private data such as addresses and social security numbers can be just as valuable to cybercriminals as valid credit card details can be to thieves - if not more so. Lock yours down with our tips.

We Live Security
DECEMBER 29, 2014
Like many others, I was enchanted by The Hobbit (and later Lord of the Rings) at a young age - long before Peter Jackson turned J R R Tolkien's middle-earth fantasy books into a series of blockbuster movies.

We Live Security
DECEMBER 29, 2014
Fingerprint biometrics are entering the mainstream as a security measure, with both Apple and Samsung relying on readers to secure their flagship phones - but biometrics may not be as secure as many believe.

We Live Security
DECEMBER 22, 2014
Barack Obama promises that the United States will respond to the Sony hack, and North Korea drops off the internet. Is there a connection?

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

We Live Security
DECEMBER 19, 2014
Hackers can eavesdrop on your phone calls and text messages even with cell networks using "the most advanced encryption available" according to The Washington Post.

We Live Security
DECEMBER 18, 2014
The nonprofit organization that looks after name and internet domains has been hit by a spear phishing hack that has compromised company data, reports The Register.

NopSec
DECEMBER 14, 2014
Usually I am not particularly a big fan of security doom scenarios, but looking at this week’s security news and the usual New Year’s security predictions I have to admit that I grew a bit concerned about the overall info security outlook. Here is the canvas: Sabotage attacks from Iran targeting US industrial control systems and critical infrastructure modeled after Stuxnet, Duqu, and Wiper are growing in frequency.

We Live Security
DECEMBER 11, 2014
Three UK firms have been fined over $500,000 for a scam that involved Android apps signing up to a subscription service, and suppressing notifications informing the victim they were being charged, according to The Guardian.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

We Live Security
DECEMBER 4, 2014
Firefox 34, the latest version of the Mozilla's popular web browser has disabled support for SSL 3.0 in reaction to the POODLE exploit, reported by We Live Security back in October.

Privacy and Cybersecurity Law
DECEMBER 1, 2014
The recent IAPP Congress in Brussels provided a platform to bring out the “big guns” on privacy. Needless to say, […].

Privacy and Cybersecurity Law
DECEMBER 2, 2014
The Article 29 Working Party published new Guidelines on the Right to be Forgotten on 26 November 2014. This is […].
Let's personalize your content