Black Hat insights: Getting bombarded by multiple ransomware attacks has become commonplace
The Last Watchdog
AUGUST 15, 2022
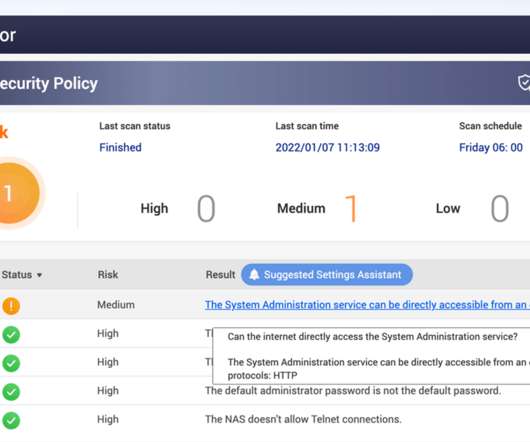
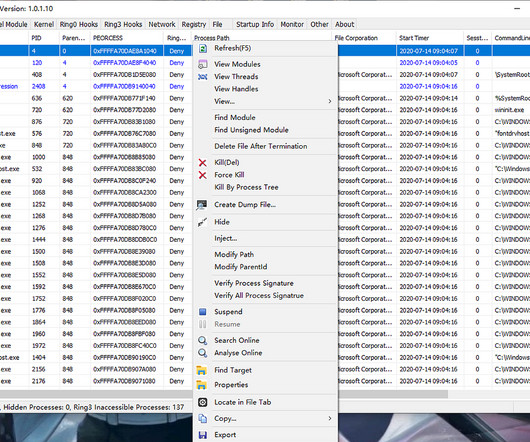
And if an enterprise is under an active ransomware attack, or a series of attacks, that’s a pretty good indication several other gangs of hacking specialists came through earlier and paved the way. Each of the three ransomware gangs encrypted whatever systems they could get their hands on; and each left its own ransom demand.






















Let's personalize your content