ViperSoftX Leverages Deep Learning with Tesseract to Exfiltrate Sensitive Information
Penetration Testing
MAY 19, 2024
AhnLab Security Intelligence Center (ASEC) has uncovered a new tactic employed by the notorious ViperSoftX malware.

Penetration Testing
MAY 19, 2024
AhnLab Security Intelligence Center (ASEC) has uncovered a new tactic employed by the notorious ViperSoftX malware.

eSecurity Planet
DECEMBER 30, 2020
To ease these burdens, SECaaS and SOCaaS vendors have emerged as cloud-based security as a service that can collect, analyze, and correlate your information from diverse systems and applications — turning former headaches into actionable information security intelligence. Security as a Service (SECaaS) .
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

NopSec
SEPTEMBER 12, 2016
Reducing the Risk of a Ransomware Attack – The Human Element According to the IBM Security Services 2014 Cyber Security Intelligence Index, human error is responsible for almost 95% of all security incidents. Ransomware is no different. Rather, the goal is to identify where processes can be improved.

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Beyond Identity Identity management 2020 Private Expel Managed security service 2016 Private Tigera Zero trust for K8s 2016 Private Intrinsic Application security 2016 Acquired: VMware HackerOne Penetration testing 2015 Private Virtru Data encryption 2014 Private Cloudflare Cloud infrastructure 2010 NYSE: NET.
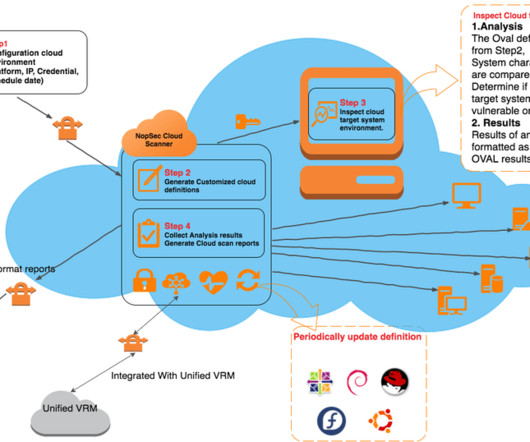
NopSec
JULY 13, 2016
Particularly in the AWS – Amazon Web Services – environment, in order to assess vulnerabilities in the public cloud each vulnerability scan and/or penetration test needs to be cleared with AWS by filling an authorization form in advance. This creates a convoluted administrative process to authorize the scan in advance.

Spinone
DECEMBER 26, 2018
Social engineering attacks , including phishing, spam, and viruses introduced via clickable links within e-mail affected 80% of the banking institutions in 2016. Aimed at reducing corporate vulnerability to insider threats, info security professionals should regularly monitor the most important infrastructure locations.
Let's personalize your content