Role of Context in Threat Detection
Anton on Security
DECEMBER 28, 2020
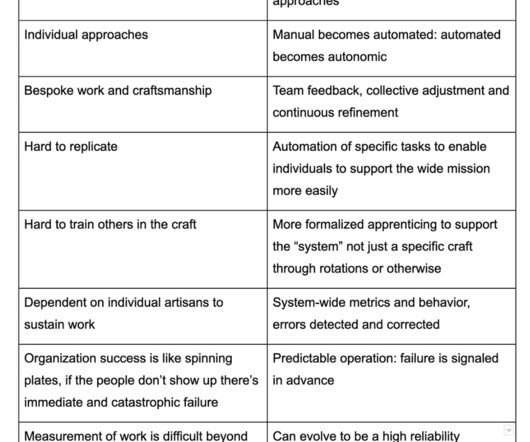
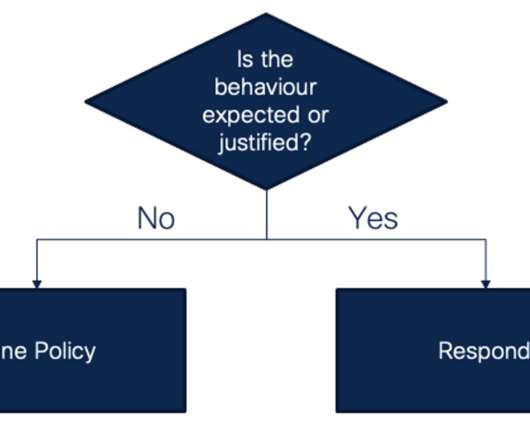
The debate focused on the role of context in threat detection. Specifically, it is about the role of local context (environment knowledge, organization context, site details, etc) in threat detection. Can threat detection work well without such local context? Now, some of you will say “yes, of course!”
















Let's personalize your content