New iLOBleed Rootkit, the first time ever that malware targets iLO firmware
Security Affairs
DECEMBER 30, 2021
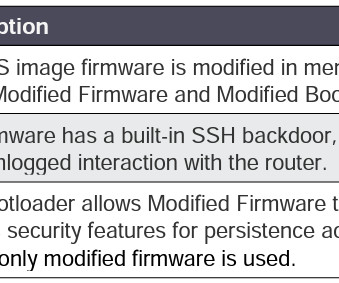
A previously unknown rootkit, dubbed iLOBleed, was used in attacks aimed at HP Enterprise servers that wiped data off the infected systems. The Integrated Lights-Out is a proprietary embedded server management technology from Hewlett-Packard Enterprise which provides out-of-band management facilities. ” continues the report.













Let's personalize your content