Implementing and Maintaining Security Program Metrics
NopSec
NOVEMBER 19, 2021
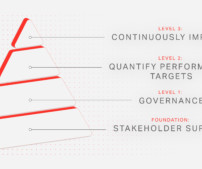
A strong commitment to information security within the highest levels of an organization’s executive management team helps protect the security program from organizational pressures and budget limitations. Level 1: Governance. Foundation: Stakeholder support. Level 2: Quantify Performance Targets.











Let's personalize your content