Implementing and Maintaining Security Program Metrics
NopSec
NOVEMBER 19, 2021
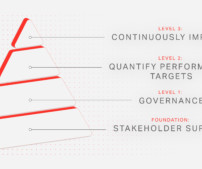
A strong commitment to information security within the highest levels of an organization’s executive management team helps protect the security program from organizational pressures and budget limitations. Information security performance goals and objectives must be easily obtainable, feasible to measure, and repeatable.












Let's personalize your content