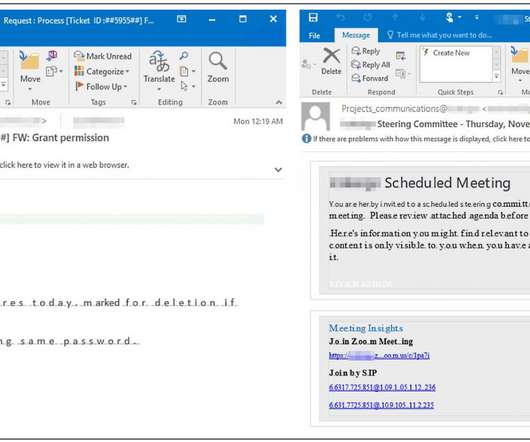
Office 365 phishing campaign uses redirector URLs and detects sandboxes to evade detection
Security Affairs
NOVEMBER 18, 2020
Microsoft is tracking an ongoing Office 365 phishing campaign aimed at enterprises that is able to detect sandbox solutions and evade detection. Microsoft is tracking an ongoing Office 365 phishing campaign that is targeting enterprises, the attacks are able to detect sandbox solutions and evade detection.













Let's personalize your content