Staying a Step Ahead of the Hack
Webroot
DECEMBER 11, 2020
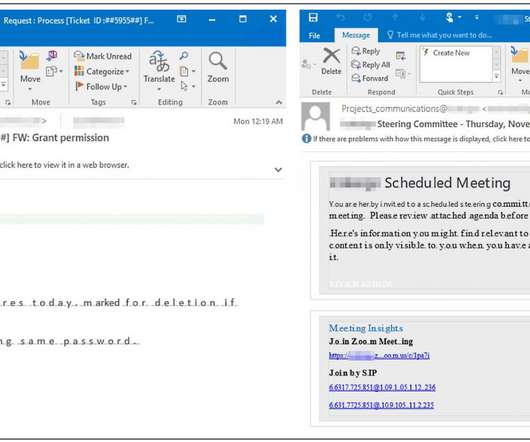
Hackers, never at a loss for creative deception, have engineered new tactics for exploiting the weakest links in the cybersecurity chain: ourselves! Social engineering and business email compromise (BEC) are two related cyberattack vectors that rely on human error to bypass the technology defenses businesses deploy to deter malware.














Let's personalize your content