Microsoft spotted multiple malspam campaigns using malware-laced ISO and IMG files
Security Affairs
MAY 4, 2020
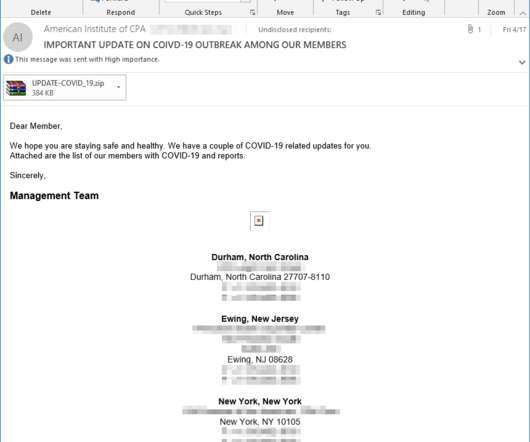
Microsoft warns of threat actors targeting organizations with malware-laced ISO and IMG files aimed at delivering a remote access trojan. Microsoft advanced machine learning threat detection models detected multiple malspam campaigns distributing malware-laced ISO.












Let's personalize your content