Feds Charge Five Men in ‘Scattered Spider’ Roundup
Krebs on Security
NOVEMBER 21, 2024
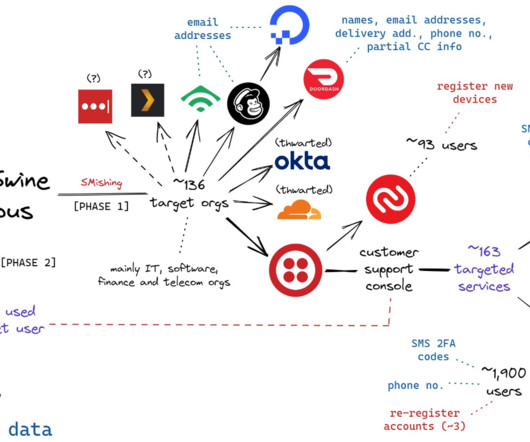
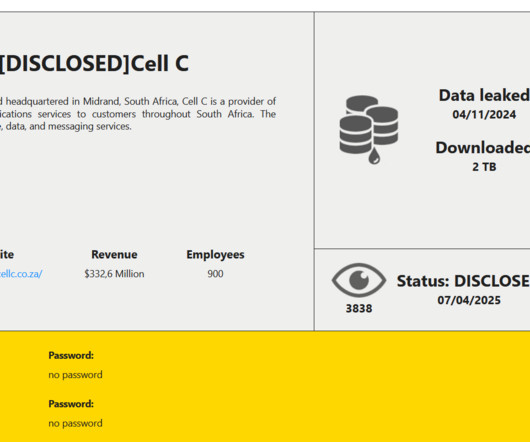
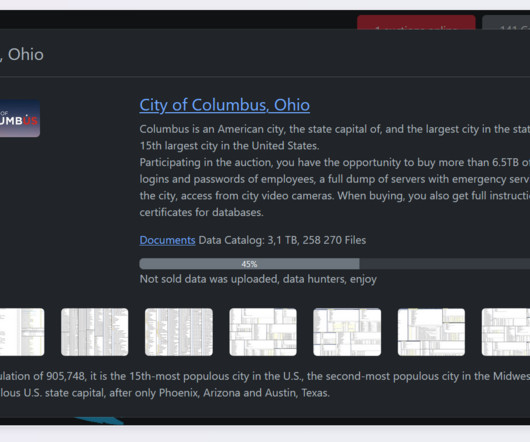
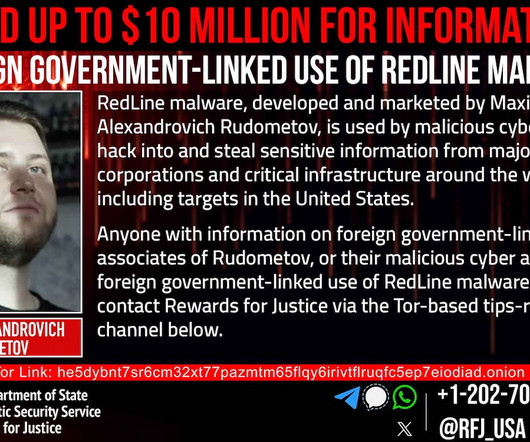
“The defendants allegedly preyed on unsuspecting victims in this phishing scheme and used their personal information as a gateway to steal millions in their cryptocurrency accounts,” said Akil Davis , the assistant director in charge of the FBI’s Los Angeles field office.















































Let's personalize your content