RSAC insights: Malware is now spreading via weaponized files circulating in data lakes, file shares
The Last Watchdog
JUNE 3, 2022
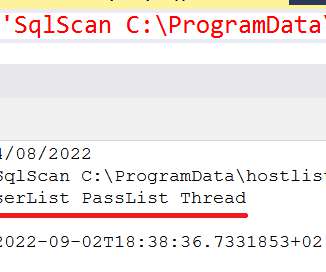
“The trend that we’re seeing is that more than 30 percent of the content flowing into data lakes is from untrusted sources,” he says. “It’s It’s documents, PDFs, CSV files, Excel files, images, lots of unstructured data; we track 150 different file types. This is the dark side of digital transformation.



















Let's personalize your content