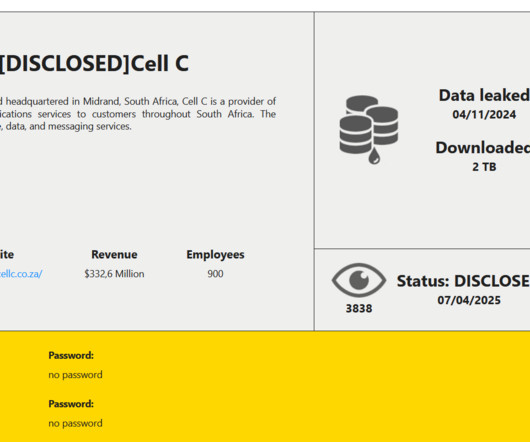
South African telecom provider Cell C disclosed a data breach following a cyberattack
Security Affairs
APRIL 13, 2025
. “Cell C is aware that data compromised in the recent cybersecurity incident has been unlawfully disclosed by RansomHouse, the threat actor claiming responsibility.” “This follows a previously reported incident involving unauthorised access to unstructured data in some parts of our IT environment.”





















Let's personalize your content