Anomali ThreatStream: Threat Intelligence Product Overview and Insight
eSecurity Planet
FEBRUARY 8, 2023
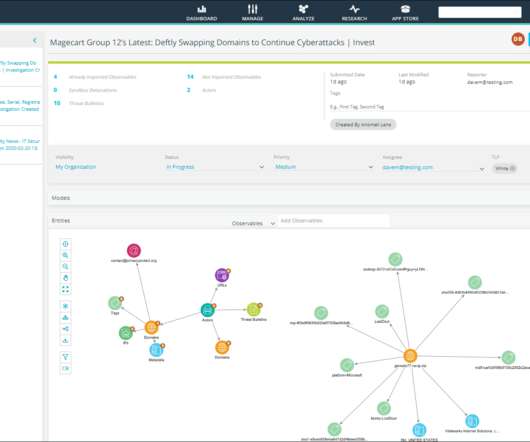
Applicable Metrics ThreatStream consumes both structured and unstructured data from hundreds of threat intelligence feeds, processing millions of Indicators of Compromise (IOCs). Anomali indicates a replacement may be in development, but has not yet provided any details.
















Let's personalize your content