How I Got Pwned by My Cloud Costs
Troy Hunt
JANUARY 23, 2022
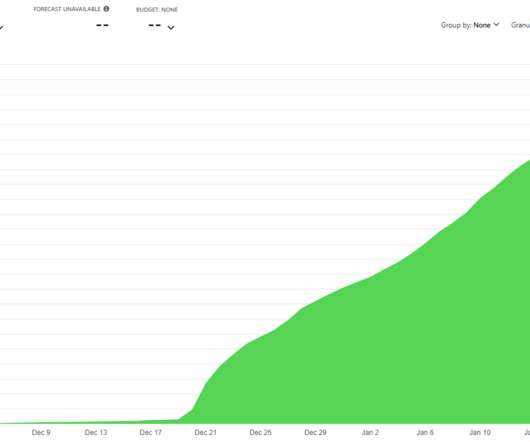
What we're talking about here is egress bandwidth for data being sent out of Microsoft's Azure infrastructure (priced at AU$0.014 per GB) so normally things like traffic to websites. ", "statusCode":200, "statusText":"Success", "durationMs":690285, "callerIpAddress":"172.68.132.54:13300",












Let's personalize your content