How to Lose a Fortune with Just One Bad Click
Krebs on Security
DECEMBER 18, 2024
More importantly, Tony recognized the voice of “Daniel from Google” when it was featured in an interview by Junseth , a podcaster who covers cryptocurrency scams. “No one gets arrested,” Daniel enthused to Junseth in the May 7 podcast, which quickly went viral on social media.



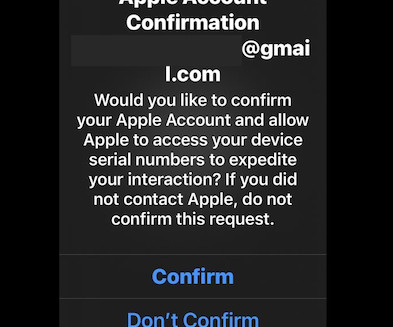














Let's personalize your content