Cloud Compliance Frameworks: Ensuring Data Security and Regulatory Adherence in the Digital Age
Centraleyes
MARCH 11, 2024
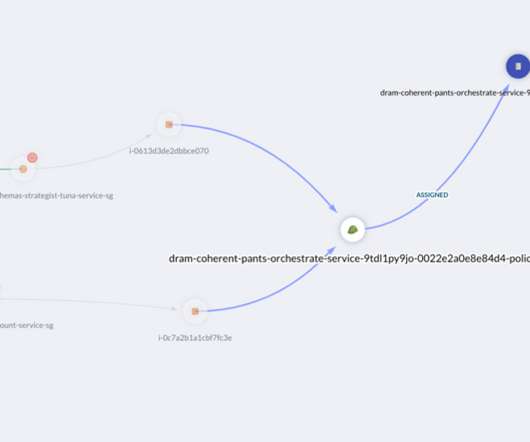
Enter cloud compliance frameworks—the mission control centers of the digital age—providing the necessary guidelines and protocols to avert crises and navigate the complexities of data security. It emphasizes key principles, offering a comprehensive approach to designing secure, reliable, and performant solutions.



























Let's personalize your content