How to Structure an Enterprise-Wide Threat Intelligence Strategy
Dark Reading
JULY 13, 2018
To keep an organization safe, you must think about the entire IT ecosystem.

 threat-intelligence how-to-structure-an-enterprise-wide-threat-intelligence-strategy
threat-intelligence how-to-structure-an-enterprise-wide-threat-intelligence-strategy 
Dark Reading
JULY 13, 2018
To keep an organization safe, you must think about the entire IT ecosystem.

eSecurity Planet
JANUARY 27, 2022
As threats mount from ransomware gangs , Russian-backed hacker groups , and other nation-sponsored attackers and as the growth in remote work makes security management increasingly complicated, many companies are finding it makes sense to turn to a managed security service provider (MSSP) for help with handling an extremely complex threat landscape.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Centraleyes
MARCH 25, 2024
How’s your vulnerability management going? Let’s explore how you can enhance your vulnerability management strategy. According to IBM’s X-Force Threat Intelligence Index , vulnerability exploitation is the second most prevalent cyberattack vector. Is it effective? What is Vulnerability Management?

CyberSecurity Insiders
JULY 19, 2021
Creating an effective threat hunting program is among the top priorities of security leaders looking to become more proactive and build active defenses. Organizations must adopt a structured process to guide their hunting activities. Why Employ a Formal Threat Hunting Framework? Source: Enterprise Detection and Response.

SecureWorld News
JANUARY 7, 2024
The integration of Governance, Risk, and Compliance (GRC) strategies with emerging technologies like Artificial Intelligence and the Internet of Things are reshaping the corporate risk landscape. A company's social responsibility strategy also falls under the scope of corporate governance.

eSecurity Planet
MAY 24, 2023
A cloud workload protection platform (CWPP) shields cloud workloads from a range of threats like malware, ransomware, DDoS attacks, cloud misconfigurations, insider threats, and data breaches. per server per month.
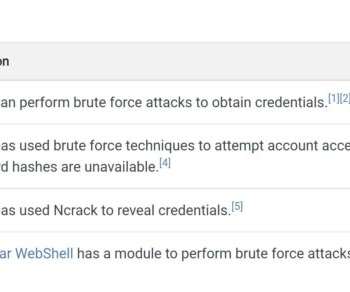
eSecurity Planet
DECEMBER 29, 2021
MITRE ATT&CK (“miter attack”) is an up-to-date and widely-used knowledge base that focuses on how attackers think and operate. It’s based on practical use cases, so companies can better evaluate security issues and get examples of common tactics and techniques used by threat actors. Detection and analytics.
Let's personalize your content